Packers continue to be a go-to tool for malware authors looking to hide their malicious code and slip past security defenses. One such packer, currently labeled as pkr_ce1a, has been spotted distributing a range of malware families, including SmokeLoader and Vidar, among others. This packer has been active for several years, with evidence suggesting its presence as far back as 2017. In this article, we’ll take a closer look at the first stage of a pkr_ce1a sample that delivers a SmokeLoader payload, breaking down its unique features and how it operates.
The pkr_ce1a packer is a highly advanced tool designed to compress and encrypt malicious payloads, making them difficult for security systems to detect. Its ability to remain active in the wild for so long—potentially since 2017—highlights its effectiveness and adaptability.
One of the more interesting features of pkr_ce1a is its use of two stable byte strings that don’t seem to serve an obvious purpose. These strings consistently appear on either side of values that are crucial to the decoding and unpacking process. While their exact role isn’t entirely clear, they may be part of the packer’s obfuscation or anti-analysis tactics, further complicating efforts to analyze and detect the malware.
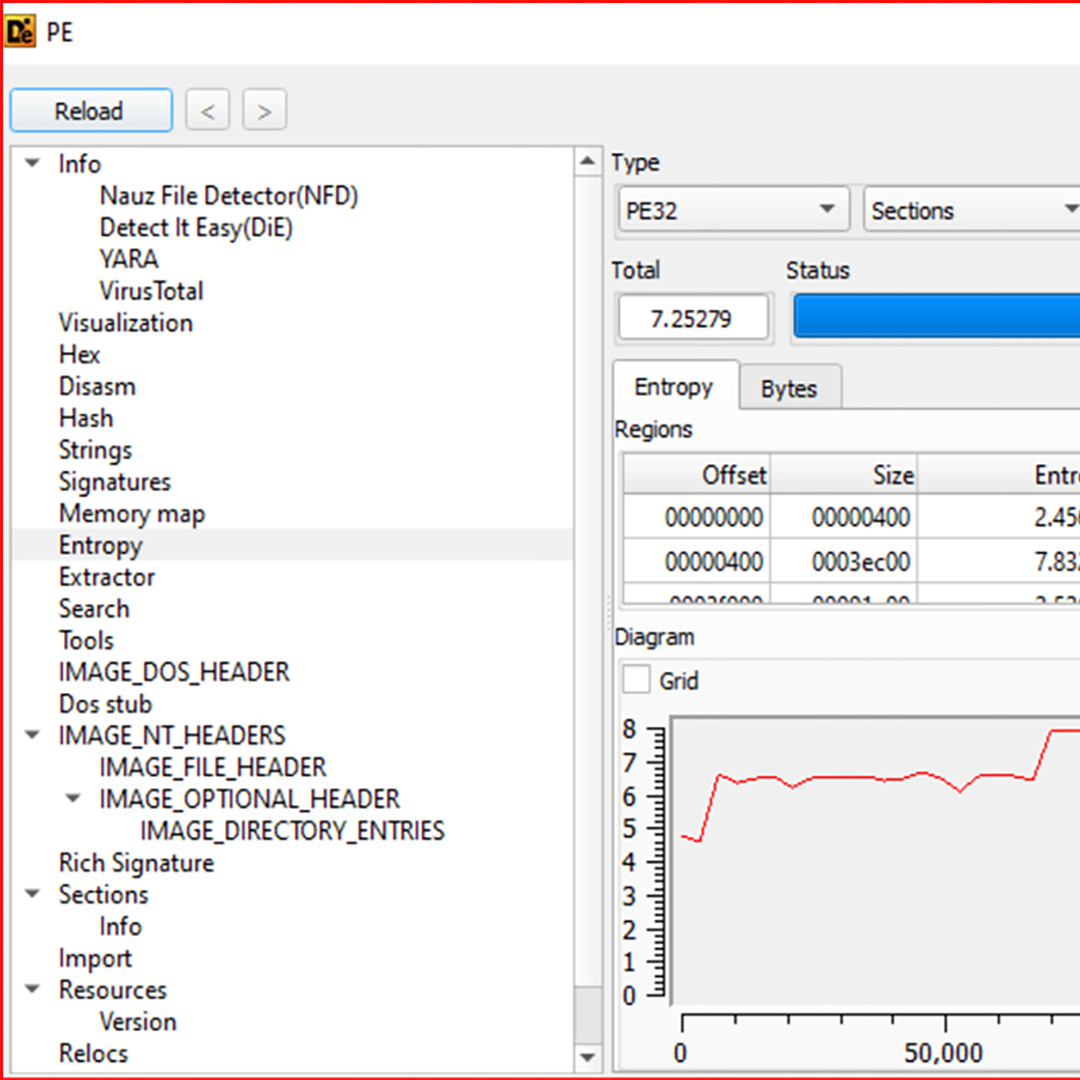
I will work on this sample: 786d66537812fd5b0bc48f67e87b4a5d, which is based on static analysis. Let us open the sample with Detect It Easy (DIE), as shown in the next figure.

I will use x64dbg to load the sample with the debugger. I will set a breakpoint on VirtualAlloc, which is used to allocate a region of memory. This process is illustrated in the next figure.
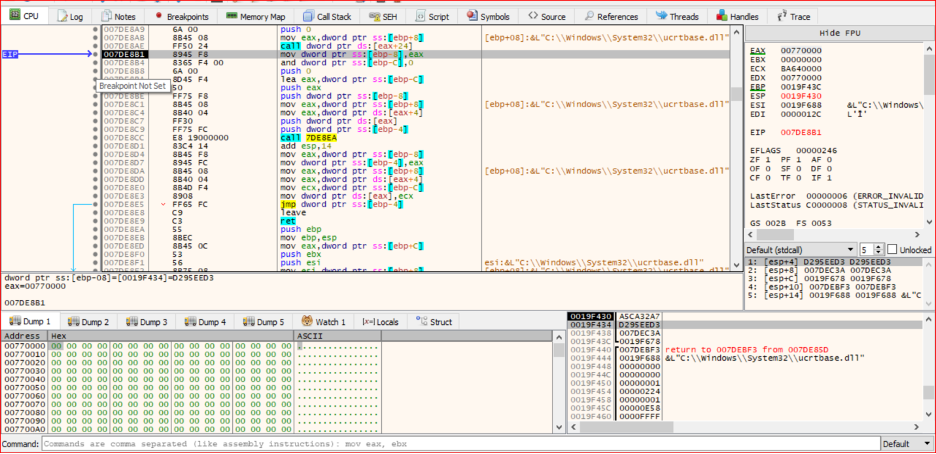
From the previous figure, we can see the allocated region of memory, which is used to load and parse the shellcode into this region.
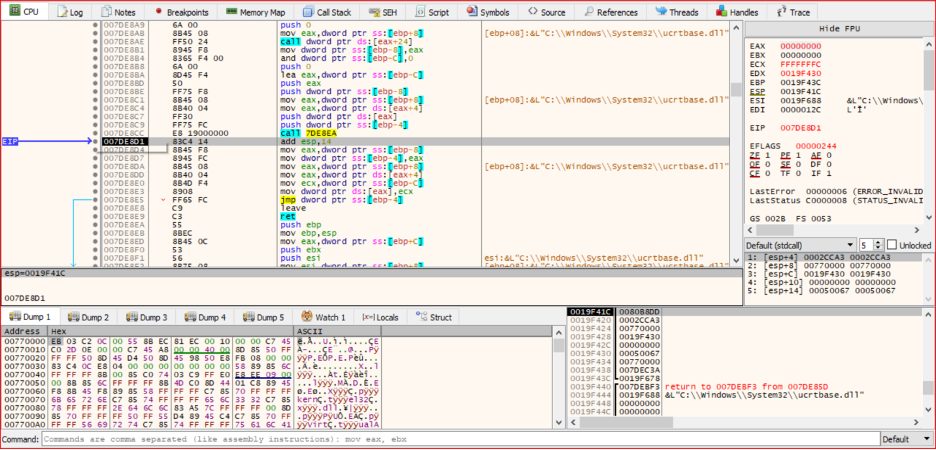
The packer will transfer execution to the shellcode. As shown, the packer attempts to jump to the shellcode's address to execute it.
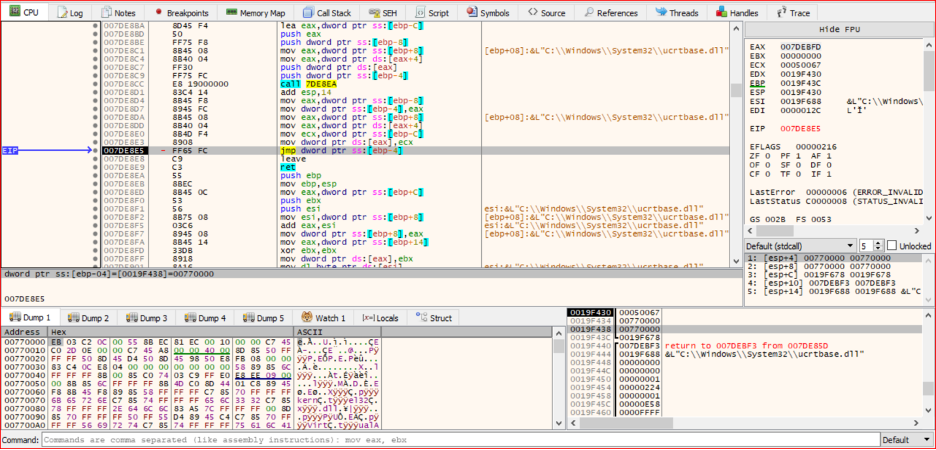
During the execution of shellcode, we can detect that shellcode used stack string techniques to obfuscate the strings of API names that will be used to unpack the packed file.
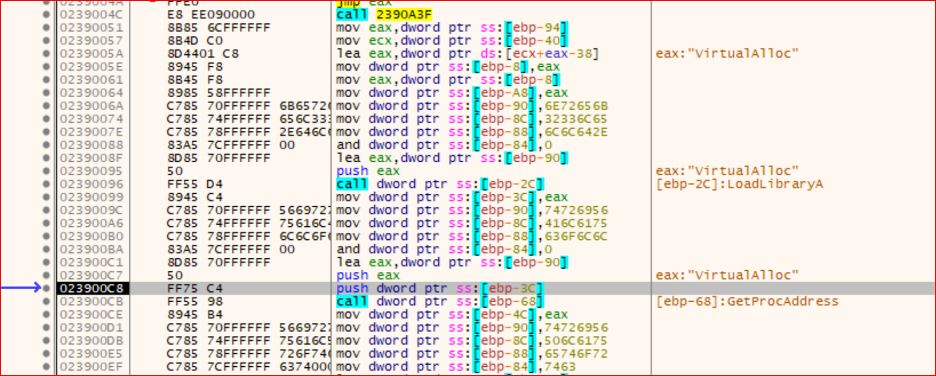
Shellcode will use a loop to write the unpacked file into memory, as shown in the next figure.
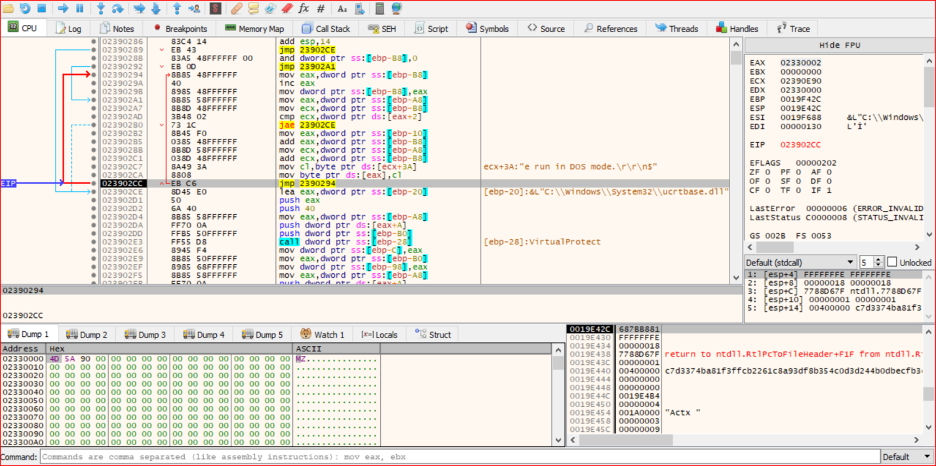
After executing the loop and parsing the unpacked file into memory, I dump the unpacked file from memory.
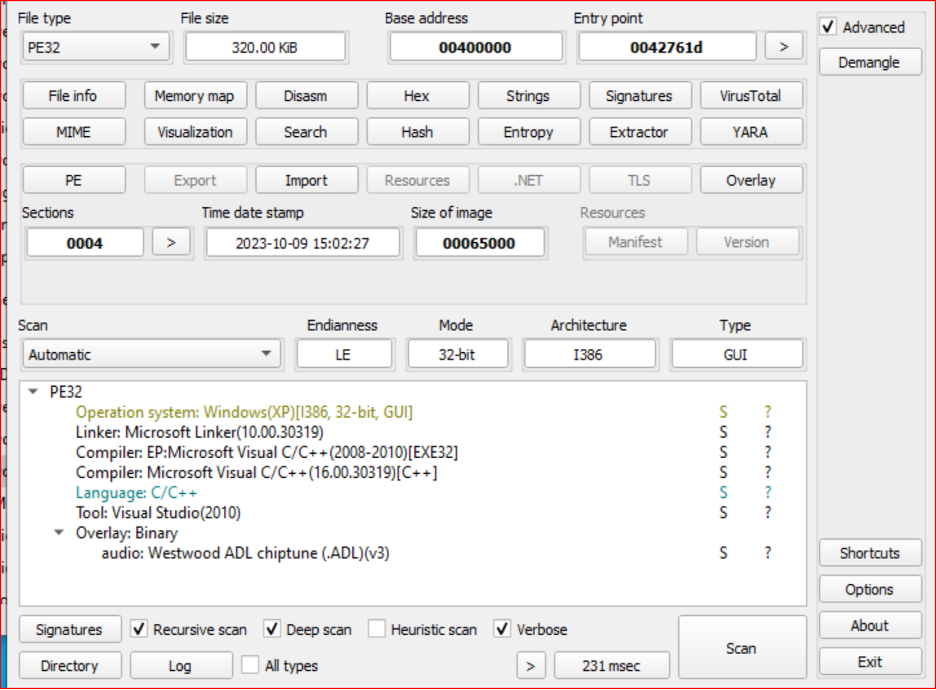
Hashes:
c7d3374ba81f3ffcb2261c8a93df8b354c0d3d244b0dbecfb3eef5f7c07c444c
Unpacking is a critical step in malware analysis, enabling analysts to reveal the concealed malicious code within packed binaries. By effectively unpacking malware, security professionals can conduct thorough analyses, develop accurate detection signatures, and implement robust defense mechanisms. This process not only aids in understanding the malware's functionality but also enhances the overall efficacy of cyber security measures.