
Qilin is a ransomware group that emerged in July 2022 and operates under a Ransomware-as-a-Service (RaaS) model.
The group primarily targets critical sectors including healthcare, finance, education, and government, with a history of disrupting major services, such as the UK NHS pathology provider Synnovis. Qilin has claimed over 300 attacks, with victims listed on its dark web leak site, and ransom demands ranging from $50,000 to $800,000.
Qilin ransomware is written in Go and Rust, enabling cross-platform attacks on Windows, Linux, and VMware environments. It employs multiple encryption algorithms, including ChaCha20, AES-256, and RSA-4096, and uses a double extortion strategy to maximize pressure on victims.
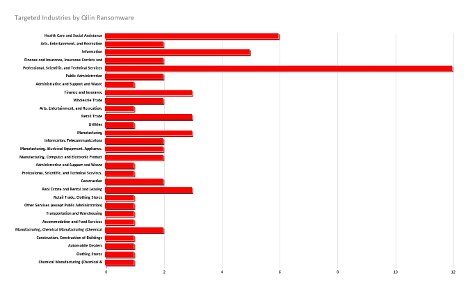
Most Targeted Industries by Qilin according to the SOCRadar data
Once Qilin completes initial access, they typically move laterally across the victim’s infrastructure, searching for data to encrypt.
During the encryption process, the actors place a ransomware note of the system, which provides instructions on how to purchase the decryption key.
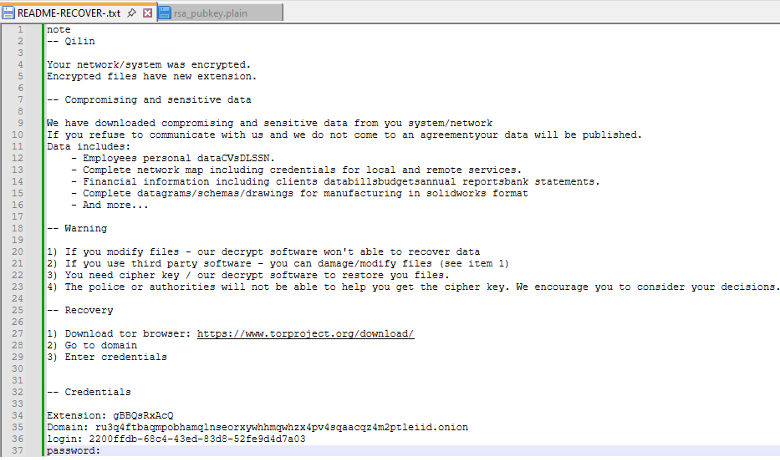
Qilin’s Ransom Note.
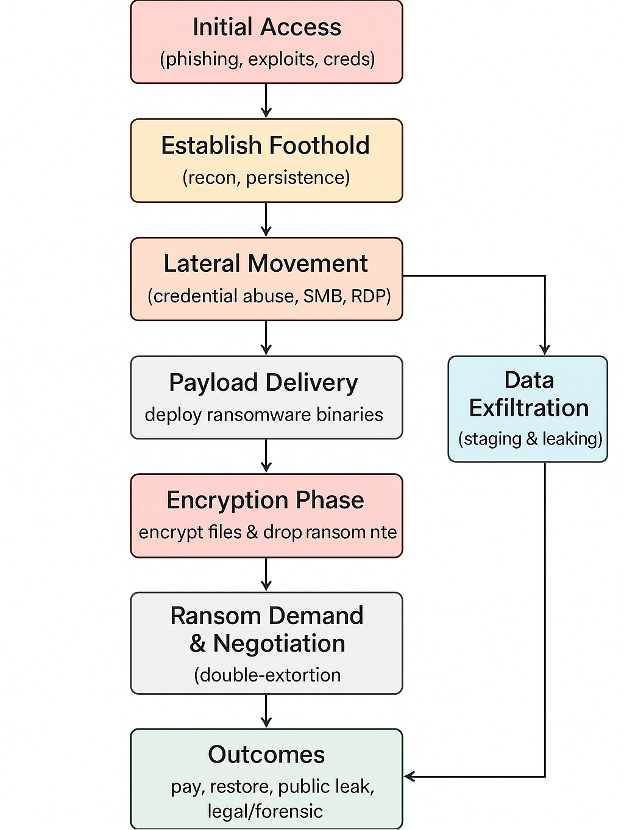
Qilin Infection Chain.
one of it is CreateMutex is using by Qilin to prevent itself from running multiple copies of the same task at the same time.
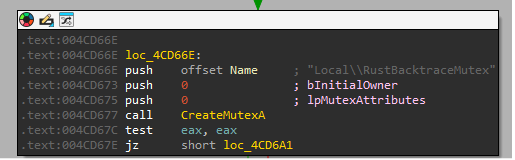
Mutex in Action.
Creates a mutex named "Local\\\\RustBacktraceMutex".
Qilin targets a long list of process of names to be terminated, as well as for the names of services to be stopped or denied.
The ransomware has an extensive list of processes and services it will attempt to terminate and stop. This list is designed to stop security software, database servers, backup tools, and other applications that could interfere with encryption or allow for recovery.
The malware iterates through the running processes and services and checks their names against the massive regex patterns in this list. If a match is found, it terminates the process and stops services.
Privilege escalation is a fundamental technique in a cyber attack where an attacker gains a higher level of access or permissions on a system than they are originally supposed to have. The core principle is to move from a limited user account to a more powerful one, typically an administrator or system-level account.
There are two proofs of concept available on GitHub by Horizon3 and sfewer-r7 that demonstrate how to exploit CVE-2023-27532 and access the backup server. However, there is no confirmed evidence that Qilin operators have utilized these exploits:
To get SYSTEM-level permissions (the highest possible on a Windows machine).
The ransomware uses an embedded tool (Mimikatz) to look at the memory of core Windows processes:
It finds a token from one of these processes that has SYSTEM or Administrator privileges and "steals" it.
Then, it also resolves symbolic links from a remote object to remote and local objects:
The Qilin deletes all system logs before initiating data encryption. After completing the encryption process, it removed all system events, erasing any traces of the malicious activities conducted by the threat actor on the host, including the clearing of Windows PowerShell and Windows System logs.
By using the following command:
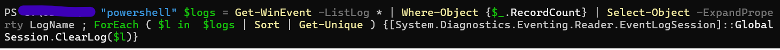
Qilin Using Command deletes all logs.
Qilin uses a multi-threading approach for the encryption process, it creates a new thread for each file it encrypts which makes it very fast.
It starts enumerating files using FindFirstFileW and FindNextFileW then it passes each file name to a new encryption thread. Note that Qilin avoids encrypting these file extensions:
The malware begins by encrypting all data on the host and any attached drives, including network shares.
File encryption is performed in multiple streams, and the data encryption can be performed using stream algorithms AES-256 CTR or ChaCha20.
Algorithm AES-256-CTR (if the CPU supports it) or ChaCha20 (if it doesn't). These are incredibly fast algorithms for encrypting large amounts of data. Keys For each file, it generates a unique, random key and nonce (a number used once) Files can be encrypted in multiple passes mode, and be encrypted three times, using three modes encryption fast, percent and normal
Algorithm RSA-4096 The unique AES/ChaCha key for each file is encrypted with the attacker's public RSA key. This creates a lock that only the attacker's private key can unlock. The encrypted key is appended to the file. The victim cannot decrypt their files without the attacker's private key.
Victims are instructed to contact the attackers through Dark Web portals or encrypted messaging platforms, which help maintain the attackers' anonymity and make it difficult for law enforcement to trace communications. Ransom payments are typically required in cryptocurrencies like Bitcoin or Monero, ensuring anonymity and reducing the chances of tracking financial transactions. However, even if the ransom is paid, there is no certainty that the attackers will provide the necessary decryption tools to restore the encrypted data.
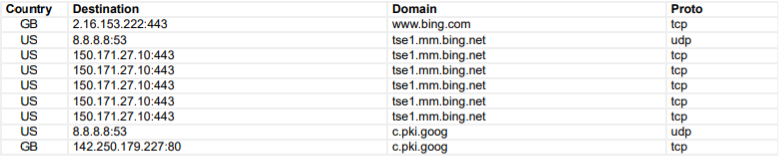
Command & Control (C2) Network Channel
SHA256: 37546b811e369547c8bd631fa4399730d3bdaff635e744d83632b74f44f56cf6
HKEY\_LOCAL\_MACHINE\\SYSTEM\\ControlSet001\\Control\\NLS\\Language