
On August 29, 2025, the cybersecurity firm Huntress identified a novel Go-based ransomware variant, which they named "Obscura." The name is derived from the ransomware's note, README_Obscura.txt.
This malware is notable for its focus on Windows Active Directory (AD) environments and its stealthy propagation mechanism, which involves leveraging the NETLOGON folder on domain controllers to spread automatically across a network.
Based on an analysis of early attacks and threat intelligence, the Obscura ransomware primarily targets enterprises with complex Active Directory (AD) architectures. Its ability to weaponize trusted AD network infrastructure is particularly dangerous for large organizations with sprawling, multi-domain environments.
Initial victimology suggests a diverse range of industries are being targeted, based on opportunistic attacks. Notable victims have been identified in sectors such as:
Attacks have been observed across several continents, indicating a broad geographic scope for the Obscura operators. Confirmed victims have been reported in:
Obscura's tactics of compromising domain controllers and employing a double-extortion model indicate a deliberate focus on large, sophisticated enterprise targets rather than small businesses or individual users. The group prioritizes high-value networks to maximize potential payouts.
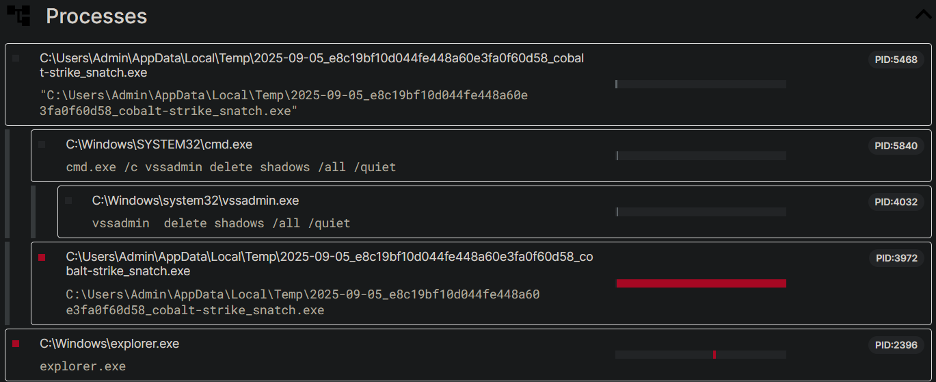
Figure (1): Processes Tree
When Obscura starts, it checks the status of an environment variable named DAEMON. If the variable is set to 1, it drops the ransom note and proceeds with encryption. If the variable is not present or is set to 0, it executes a series of functions to prepare the system for encryption.
In daemon mode (with DAEMON=1), Obscura was executed. It retrieves the threat actor's 32-byte public key by decoding a hardcoded base64 string within the executable. Then performs system reconnaissance by enumerating all storage devices, calculating their capacities, and creating a comprehensive map of all available drives and their storage sizes for encryption.
Obscura checks the status of an environment variable called DAEMON. If the value setting equal 1 will drop the ransom note and continue with encryption. If it equals 0 or non-present, it will run a chain of functions responsible to prepare it for encryption process.
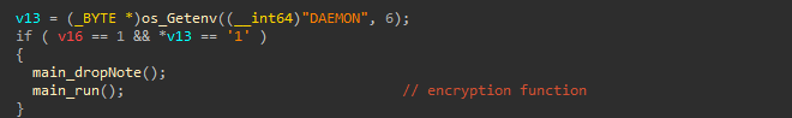
Figure (2): main.mian_check_status
The ransom determines the computer's role in a domain. To maps Windows domain roles to internal values. Each branch executes the same sequence of loading a role-specific string message and displaying corresponding status messages before immediately preceding to the daemon creation phase.
These messages suggest intended network propagation capabilities that were either never fully implemented or represent incomplete development, as the actual code contains no lateral movement functionality beyond the local encryption routine.
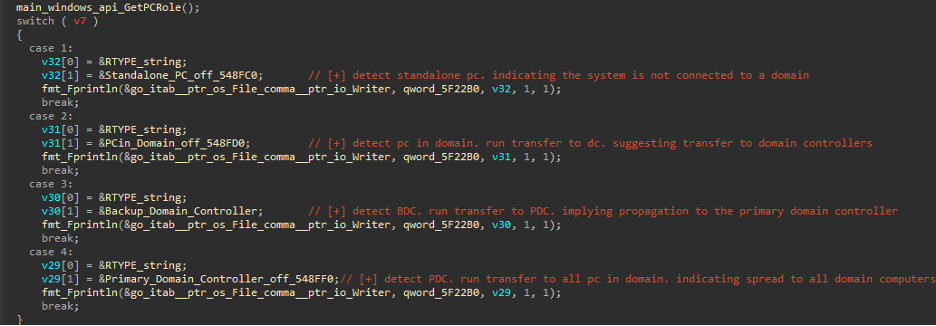
Figure (3): Network_Footprinting_The _Domain_Role_Check
Obscura Ransom Checks if is running with Administrator privileges using two linear Windows security APIs calls to determine if the current process possesses administrative rights.
First calling AllocateAndInitializeSid to Creates a Security Identifier for the Built in Administrators group. Following successful SID creation, calls CheckTokenMembership to Checks if current process token is member of Administrators group.
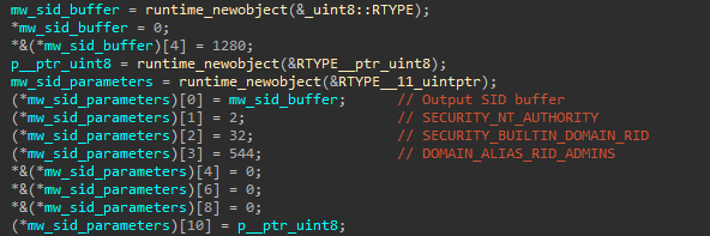
Figure (4): Privilege check
Obscura ransomware binary is executed without administrative privileges, it will terminate itself and not proceed with the attack. This is a hard requirement embedded within its code to prevent detection and failure.
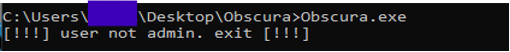
Figure (5): Run_without_admin
Obscura iterates through a predefined list of target processes. The '***' found in some process names is used to indicate a wildcard for the string matching. When a process name matches the target pattern above, the termination sequence will be executed by OpenProcess to obtain a handle to the target process with termination privileges.
If the handle is successful, TerminateProcess to forcefully terminate the process with exit code and print a success message showing the process ID and name in the format. If termination fails, the function returns an error message but continues to kill other target processes.
| Category | Process Names |
|---|---|
| Windows Defender | WinDefend MsMpEng MpCmdRun |
| Enterprise EDR |
CSFalconService SentinelAgent Crowdstrike* falcon-sensor traps* esensor* elastic-endpoint* |
| Antivirus Suites |
bdagent McAfee Avp SymCorpUI ccSvcHst AMService Emsisoft* f-secure* fsav* avast* comodo* ZoneAlarm glasswire* |
| Chinese Antivirus | 360tray 360sd ksafe avguard avgnt |
| System Monitoring | csrss_guard Winlogon EventLog Sysmon* |
| Backup Solutions |
Veeam* VeeamTransportSvc VeeamBackupSvc CommVault* NetBackup* BackupExec BEDatabase BETracker veritas* StorageCraft* druva* rubrik* |
| Database Backup | ccbackup* cbrestore* ABBService |
| Security Monitoring | ossec* wazuh* agent_m* |
| Network Storage | Syno* SynologyDrive SynologyQuickConnect |
| SIEM & Monitoring |
Splunkd SplunkForwarder Zabbix* nagios Nrpe prtg* SolarWinds* greylog* Nxlog |
| Virtualization |
VMwareHostd VMwareAuthdService VMwareNatService VMwareUSBArbZService vmware-hostd VBoxSDS VBoxHeadless VBox* vmms |
| Hyper-V Services | Vmicheartbeat Vmickvpexchange Vmicrdv vmicshutdown |
| Containerization | com.docker.service |
| Continuous integration/deployment |
gitlab-runner jenkins* TeamCity* bamboo* octopus* rundeck* |
| Automation | ansible* salt-minion |
Obscura implements a file filtering designed to avoid Prevents encryption of critical system files. The filtering system operates; it targets a 15 files extension. Then Recursive Directory Walk.
Prior to file encryption, the Obscura ransomware performs key preparation and system reconnaissance to maximize its impact. The routine proceeds as follows:
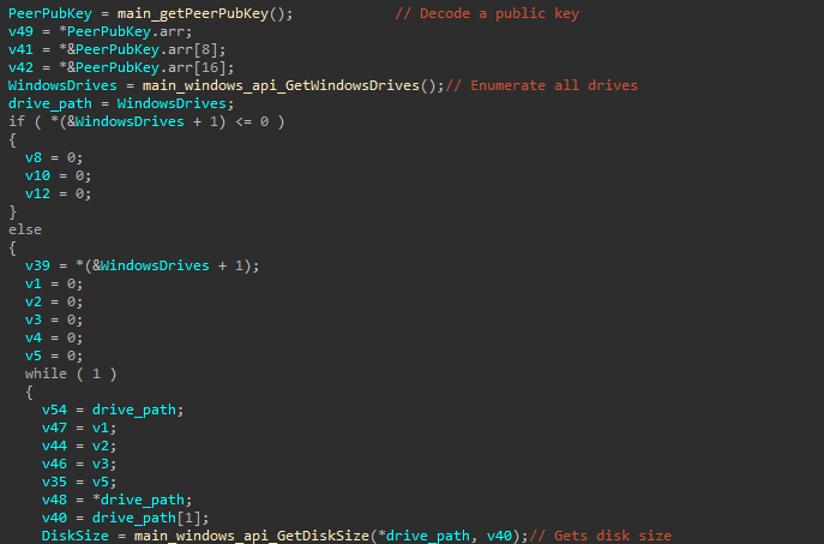
Figure (6): main_run_disk_Info
After gathering All info about Drives the Ransom make two strategies by choosing from EncryptFull or EncryptPart cause depending on the size. In Both of those two ways use EncryptFileRange but in two-way different arguments. It will take that dissension when checking the file size and comparing each file between 1 GB. If the files are 1 GB or smaller, the Ransom will call EncryptFull. That means it will encrypt the data in file from beginning to finish. For files larger than 1 GB, it will call EncryptPart, That means only encrypts the first 25% of the file by using a hardcoded ratio.
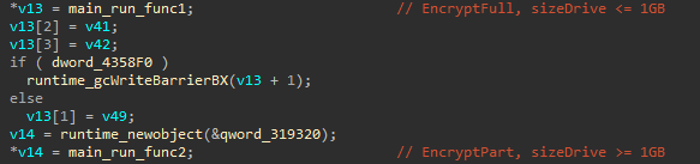
Figure (7): main_run_EncryptFull/Part
First check the Peer key length, If not equal 32 return error. for each file will Creates a temporary Curve25519 private/public key pair. The ephemeral key's public key will be stored in the footer of the encrypted file. and the private key is used only during encryption.
will compute scalar multiplication between private_key × attacker_public_key, and the result 32-byte shared secret used as the XChaCha20 encryption key. Creates a 24-byte random nonce for XChaCha20.
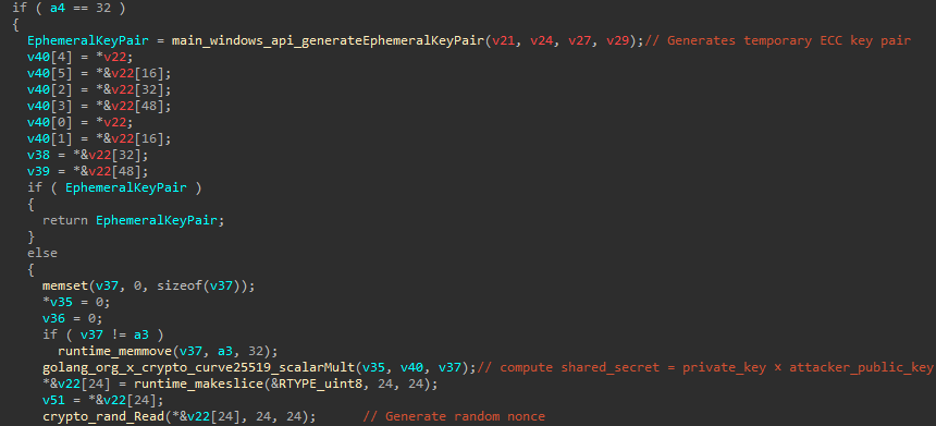
Figure (8): Encryption_Process
When the file has encrypted a file from the beginning through its end, it appends a 64-byte footer to the file containing:
After appending that footer the file renames it with the .obscura extension. The footer allows the attacker (who holds the corresponding private key) to derive the same XChaCha20 key and decrypt the file.
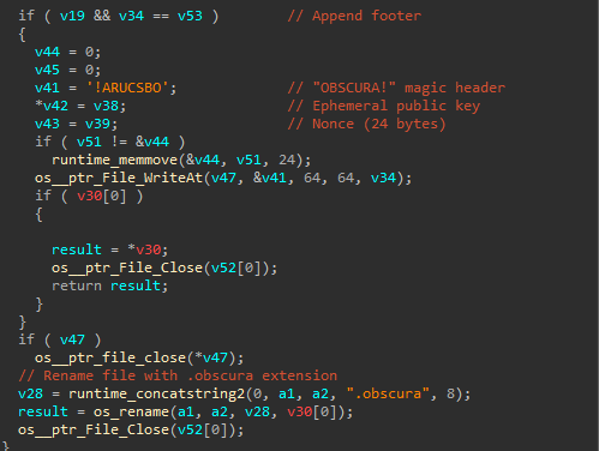
Figure (9): Encryption_Process
Before writing the encrypted file back to disk they append a 64-byte footer which is comprised of:
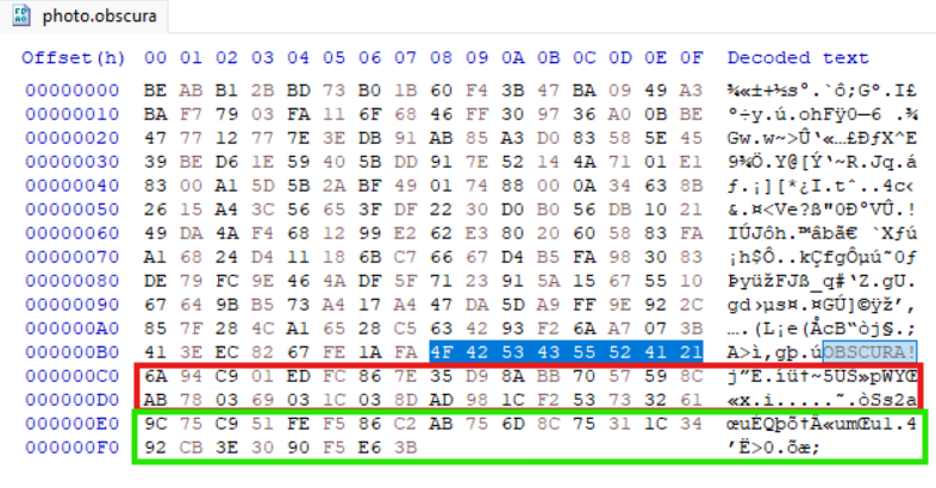
Figure (10): Demo_of_encrypted_file
The ransomware was distributed enterprise-wide by placing its binary within the Active Directory NETLOGON share (\\<DOMAIN>\NETLOGON\). This trusted domain replication mechanism automatically propagated the malware to all domain-joined systems from a central location.
The attackers established persistence using two scheduled tasks:
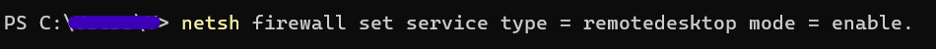
Figure (11): Persistence command
Obscura is decoding a base64-encoded ransom note from the embedded data and writing this decoded content to a file named README-OBSCURA.txt in the C:\ directory, resulting in the final path C:\README-OBSCURA.txt. If the decoding fails the ransom exits.
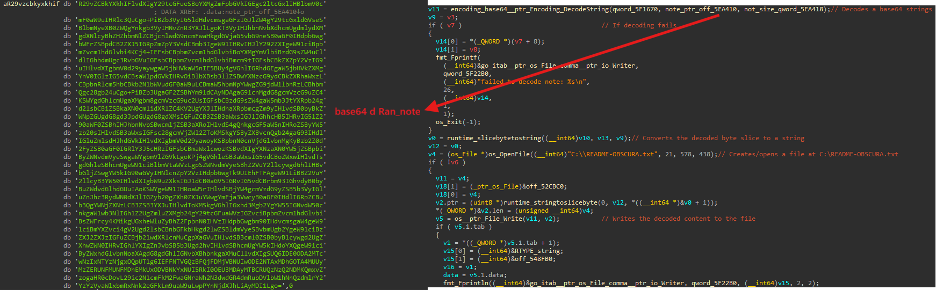
Figure (12): Decode_b64_Ransom_Note
The ransom note is dropped as README_Obscura.txt is dropped in affected directories, it directs victims to the group's website and demands payment via TOX or other anonymous and The ransom note left for victims outlines the double-extortion strategy, warning that stolen data will be leaked if the ransom is not paid.
Victims are given 240 hours to respond before the information is released.
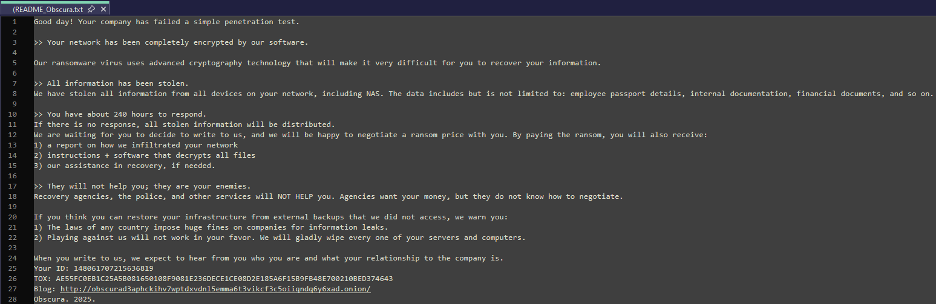
Figure (13): Ransom notes
| Tactic | Technique ID | Technique |
|---|---|---|
| Execution | T1106 | Native API |
| Persistence | T1037 | Boot or Logon Initialization Scripts |
| Persistence | T1037.001 | Logon Script (Windows) |
| Persistence | T1053 | Scheduled Task/Job |
| Persistence | T1053.005 | Scheduled Task |
| Privilege Escalation | T1546 | Event Triggered Execution |
| Defense Evasion | T1140 | Deobfuscate / Decode Files or Information |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.009 | Embedded Payloads |
| Discovery | T1069 | Permission Groups Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1087.002 | Domain Account |
| Discovery | T1497 | Virtualization / Sandbox Evasion |
| Discovery | T1497.001 | System Checks |
| Discovery | T1057 | Process Discovery |
| Lateral Movement | T1021 | Remote Services |
| Lateral Movement | T1021.002 | SMB/Windows Admin Shares |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
While the immediate damage of Obscura can be devastating, the long-term consequences of data leaks and financial extortion are even more severe. By adopting strong security practices, maintaining disciplined backup strategies, and exercising constant vigilance online, users and organizations can reduce their exposure to this destructive form of malware.