
In today’s digital-first environment, businesses and individuals are increasingly vulnerable to cyber threats that occur in real time. With attackers deploying sophisticated methods, including AI-driven exploits, defending against these threats requires equally advanced, real-time strategies. Delayed responses to cyber incidents can result in significant financial losses, compromised data, and irreparable damage to brand reputation.
Proactive real-time defense empowers organizations to move beyond traditional reactive measures. By integrating automated systems, leveraging advanced threat intelligence, and fostering a culture of vigilance, companies can ensure that they stay ahead of the evolving threat landscape.
Cybercriminals now employ automation, social engineering, and zero-day exploits to outpace traditional defenses. Attack campaigns are increasingly tailored to exploit specific vulnerabilities, often utilizing AI to bypass standard detection systems. The use of ransomware-as-a-service (RaaS) platforms has made sophisticated attacks accessible even to low-skill adversaries.
This evolution has highlighted the urgency of adopting real-time detection and response systems to neutralize threats before damage occurs. Industries such as healthcare, finance, and critical infrastructure are particularly high-value targets for attackers, making robust real-time defenses a necessity.
By addressing these challenges through technology, process optimization, and workforce development, organizations can build a resilient defense strategy tailored for the demands of modern cybersecurity.
Types of Cyber Attacks
Characteristics of Real-Time Threats
The Cost of Slow Responses
Continuous Monitoring
Implementing robust monitoring systems ensures 24/7 visibility into network activity. This proactive approach allows organizations to detect and respond to anomalies as they occur.
Automated Incident Response
Automation tools reduce the reliance on manual intervention, enabling faster and more consistent responses to threats.
Threat Intelligence
Integrating threat intelligence offers actionable insights by correlating internal logs with external threat data.
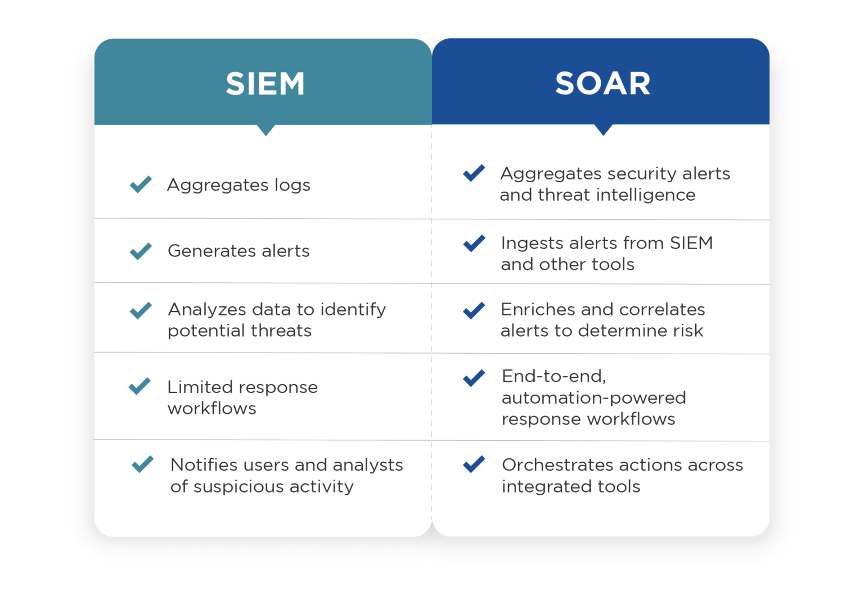
SIEM and SOAR Platforms
SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) platforms form the backbone of a real-time defense strategy.
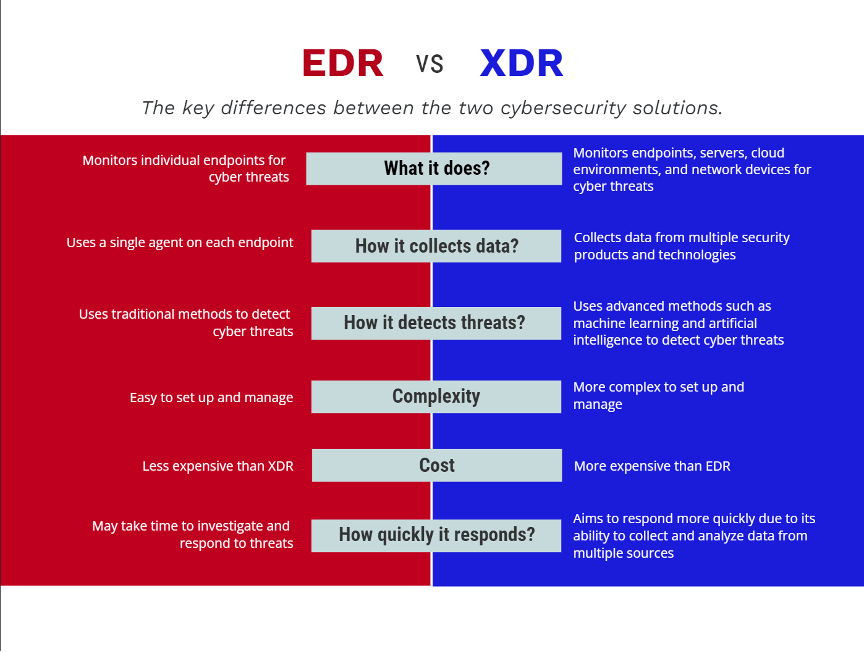
Endpoint Detection and Response (EDR/XDR)
EDR and XDR tools provide real-time visibility into endpoint activities, enabling quick identification and containment of threats.
Machine Learning and AI Applications
AI-powered systems are revolutionizing real-time defense by enhancing detection and response capabilities.
Role of Cloud Security Tools
With the increasing adoption of cloud infrastructure, specialized tools are essential for securing dynamic environments.
Integrating IoT Security Measures
As IoT devices proliferate, securing these endpoints is crucial for real-time defense.
Proactive Threat Hunting
Tools for Threat Hunting: KQL (Kusto Query Language), Elastic Stack.

Microsegmentation and Zero Trust

Rapid Containment Mechanisms
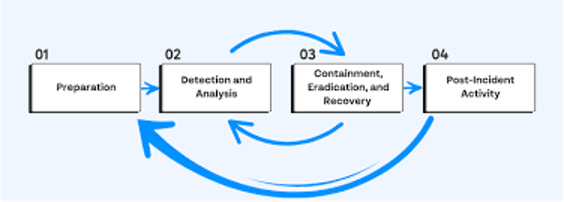
Incident Escalation Protocols
Role of Cybersecurity Playbooks
Case Study 1: Preventing a Ransomware Outbreak
Challenge: A large healthcare provider faced a ransomware attack targeting critical patient records.
Solution: Endpoint Detection and Response (EDR) tools identified unusual encryption patterns.
Outcome: The infected endpoints were isolated within seconds, preventing widespread data encryption.
Case Study 2: Mitigating Insider Threats in Finance
Challenge: A financial institution detected unauthorized data access by a privileged user.
Solution: Behavioral analytics tools flagged unusual access patterns during off-hours.
Outcome: The user's actions were halted, preventing data exfiltration.
Case Study 3: Securing IoT in Smart Manufacturing
Challenge: Compromised IoT devices were exploited to launch a DDoS attack.
Solution: Network segmentation and IoT-specific threat detection isolated the affected devices.
Outcome: The attack was neutralized without disrupting production.
Lessons Learned
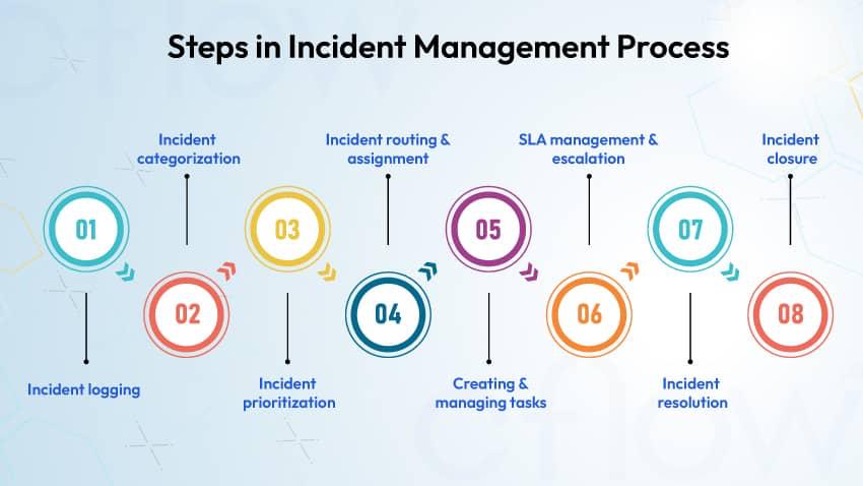
Recommended Platforms and Tools
Training and Certification Options: SANS Institute, CompTIA Security+, GIAC
Articles:
Research Papers:
Blogs:
Open-Source Resources:
Step-by-Step Guide for Organizing an Incident Response Drill:
The Path Forward: Invest in training, adopt zero trust, embrace cloud-native security, prepare for quantum threats, and foster a culture of security.
"Cybersecurity is a race against time; the faster you detect and respond, the stronger you protect."