I. Introduction: The Silent Witness in the Digital World
Imagine that a sophisticated cyberattack recently targeted a major financial
institution. The attackers, operating with stealth and precision, bypassed
initial security layers. Weeks went by before the breach was detected, and the
damage was substantial. How did they go unnoticed for so long? The clues, it
turned out, were hidden in plain sight, buried within the institution’s vast
log data — a silent witness to the unfolding crime. This scenario, inspired by
real-world events like the SolarWinds and Equifax breaches, highlights a
critical truth:
log analysis is no longer just a routine IT task; it’s a crucial art form
in the cybersecurity landscape.
In today’s world of escalating cyber threats and increasingly complex IT
environments, relying solely on firewalls and intrusion detection systems
(IDS) is insufficient. We must become adept at sifting through the digital
breadcrumbs left behind in log files. This blog post is for experienced
security professionals, system administrators, and analysts who are ready to
elevate their log analysis skills to an advanced level. We will delve into
sophisticated techniques such as log aggregation, data reduction, correlation,
anomaly detection, and threat intelligence integration, all with the aim of
uncovering hidden threats that traditional security tools might miss.
II. Beyond the Basics: Advanced Log Analysis Techniques
A. Log Aggregation and Centralization: Taming the Data Deluge
In a modern enterprise, logs are generated by a dizzying array of sources:
servers, applications, network devices, cloud services, and endpoints.
Analyzing them in their raw, distributed state is a nightmare. The first step
towards mastery is log aggregation and centralization.
-
Challenges: Imagine a company with a hybrid infrastructure—on-premise
servers, AWS instances, and Azure functions. Each platform generates logs in
different formats and locations.
-
Solutions: This is where log management solutions like the
ELK stack (Elasticsearch, Logstash, Kibana), Splunk, or
Graylog come in.
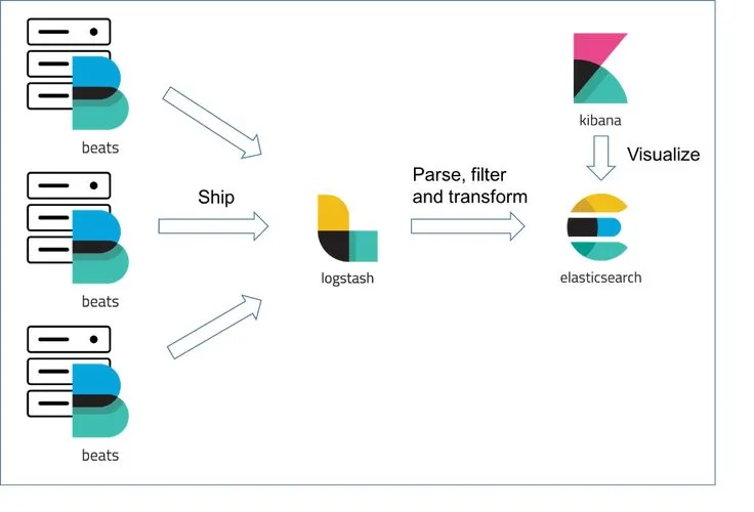
-
Logstash can be configured to ingest logs from various sources, parse
them, and forward them to Elasticsearch.
-
Elasticsearch indexes the logs for fast searching and analysis.
-
Kibana provides a web interface for visualizing and exploring the
data.
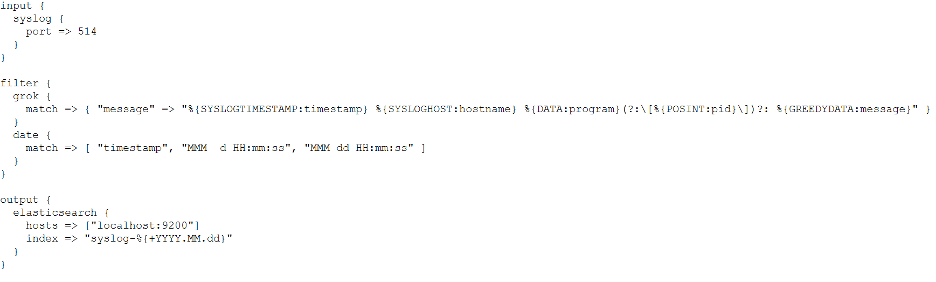
-
Normalization and Standardization: These tools help normalize
disparate log formats into a common schema. Consider standards like
CEF (Common Event Format) or the principles of syslog.
Well-structured data is crucial for efficient querying.
-
Schema Design Consideration: Using the
@timestamp field
for time will allow the use of many built-in features.
B. Data Reduction and Filtering: Finding the Needle in the Haystack
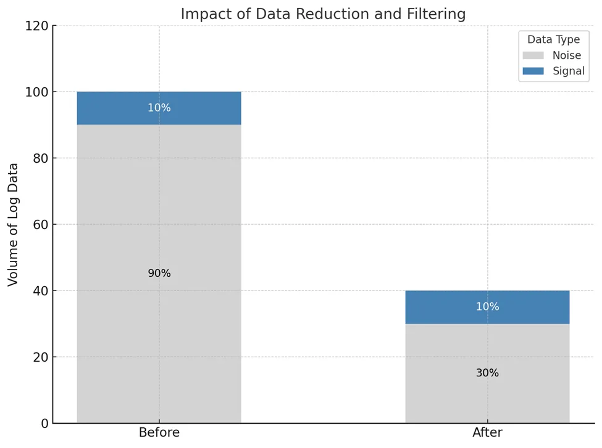
Raw logs are notoriously noisy. Effective analysis requires intelligent
filtering to focus on the most relevant events.
-
The Noise Problem: A typical web server can generate thousands of log
entries per minute. Most are benign, but buried within them might be signs
of an attack.
-
Advanced Filtering Techniques:
-
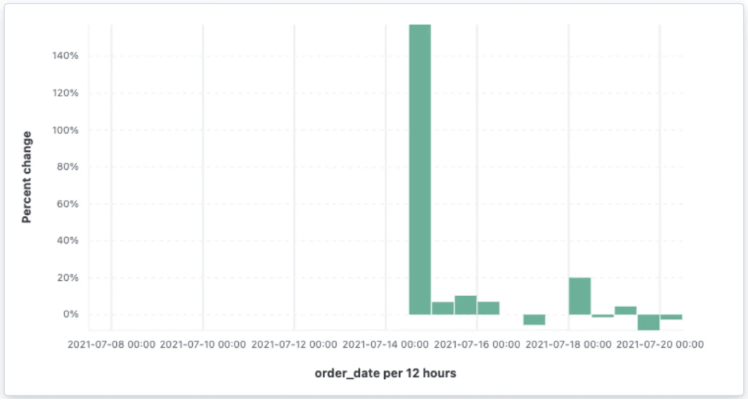
Baselining: Establish a "normal" baseline of activity. For
example, track the average number of failed login attempts per hour.
Deviations from the baseline can then trigger alerts.
-
Whitelist/Blacklist: Maintain dynamically updated lists of known
good/bad IP addresses, domains, or user agents, using them to include or
exclude the traffic related from your analysis, it will reduce the noise
and help to focus on the most important.
| Technique |
Security type |
Default Setting |
When to Use |
Main Drawback |
| Whitelist |
Trust-centric |
Always Deny |
Strictly limit access to known good sources |
Difficult to maintain |
| Blacklist |
Threat-centric |
Always Allow |
Block known malicious sources |
Never-ending process |
| Greylist |
Threat-centric |
Quarantine, then investigate |
Quarantine potentially malicious sources |
Can block legitimate sources |
-
Regular Expression (Regex) Mastery: Use Regex to extract
specific patterns from log entries.
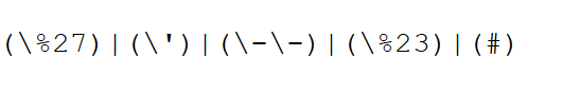
-
Statistical Outlier Detection: Use simple statistical methods. For
example, calculate the Z-score of failed login attempts. A high Z-score
(e.g., ≥ 3) indicates an unusual spike.

C. Event Correlation and Sequencing: Connecting the Dots
Isolated events might seem harmless, but when correlated, they can reveal a
sophisticated attack.
-
Real-World Scenario: An attacker might first probe a web server for
vulnerabilities (port scanning), then attempt to exploit a specific
vulnerability (e.g., SQL injection), and finally gain unauthorized access.
Each event generates a log entry.
-
Correlation Rules: Example: Failed login followed by successful login
from the same IP.
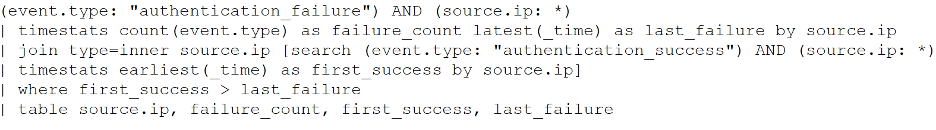 This Splunk query searches for failed login attempts followed by a
successful login from the same IP address within a defined time window,
which could indicate a brute-force attack.
This Splunk query searches for failed login attempts followed by a
successful login from the same IP address within a defined time window,
which could indicate a brute-force attack.
-
Stateful Analysis: Track sequences over time. For example, detect a
slow port scan followed by targeted exploit attempts.
-
Visualization: Tools like Neo4j (graph database) can be used
to visualize relationships between events, making attack patterns more
apparent.
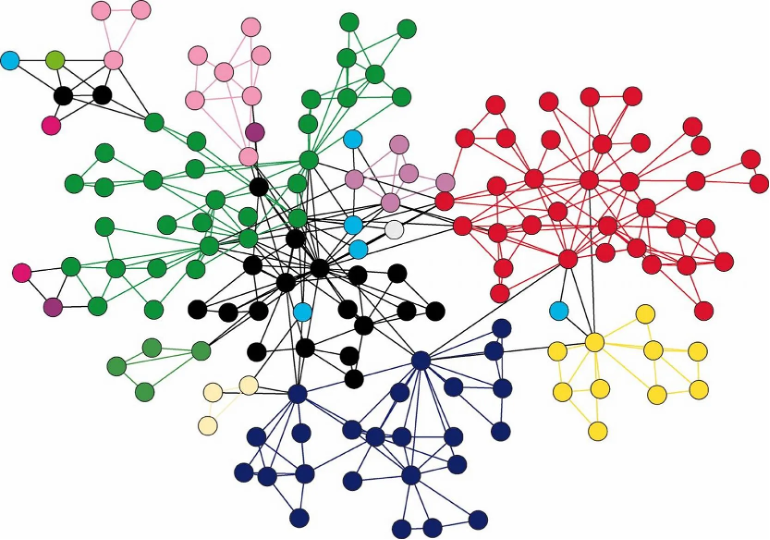
D. Anomaly Detection and Behavioral Analysis: Beyond Signatures
Signature-based detection is reactive. Anomaly detection, particularly User
and Entity Behavior Analytics (UEBA), allows us to proactively identify
unusual patterns that might indicate zero-day attacks or insider threats.
-
UEBA in Action: Imagine an employee who typically accesses files on a
particular file share during business hours. Suddenly, they start accessing
files at 3:00 AM and transferring large amounts of data. This deviation from
their established baseline is a red flag.
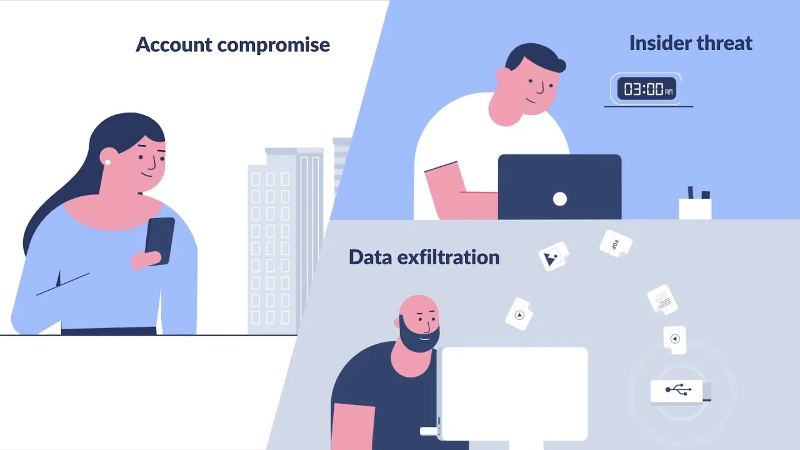
- Machine Learning (ML) for Anomaly Detection:
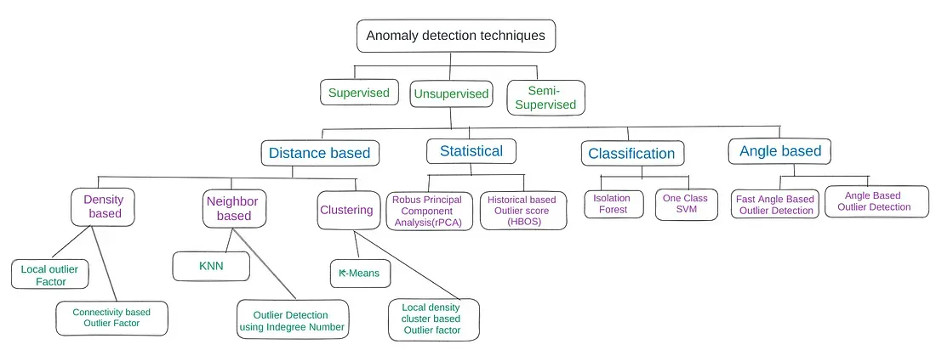
-
Example (Unsupervised Learning - Clustering): Use K-means clustering
to group similar user activity patterns based on log data (e.g., login
times, accessed resources, data transfer volumes). Outliers that don't fit
into any cluster are flagged as potential anomalies.
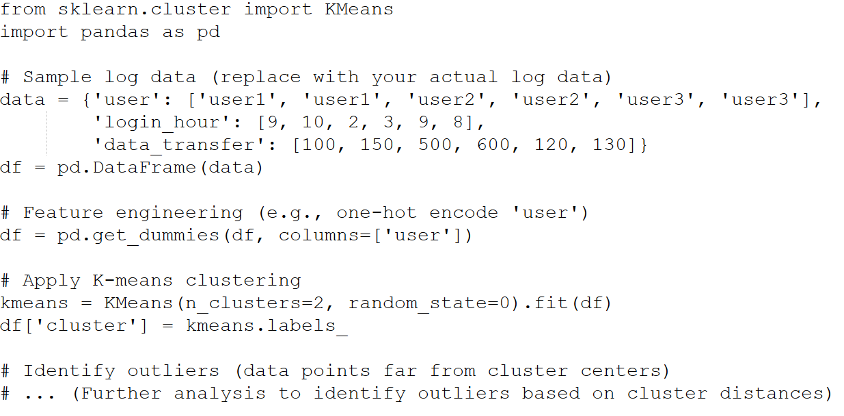
-
Challenges of ML: ML in log analysis requires high-quality data,
careful feature engineering, and ongoing model tuning.
- Example Anomalies:
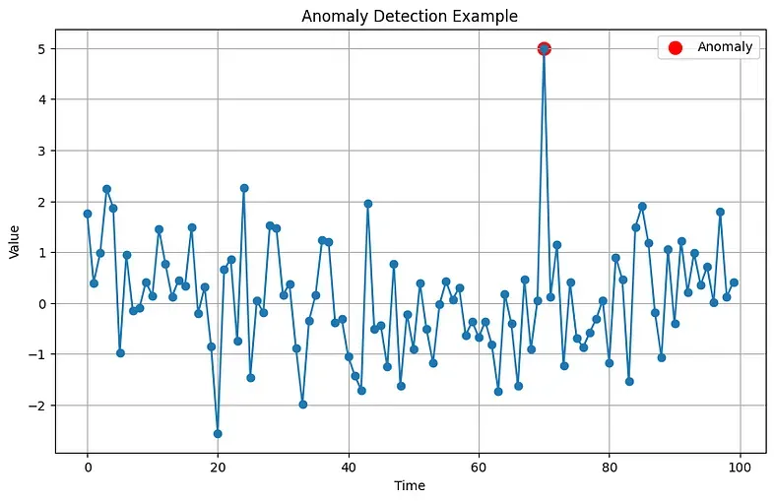
-
Unusual Login Times: A user logging in from a new geographical
location or at an odd hour.
-
Excessive Data Transfers: An unusually large amount of data being
downloaded or uploaded.
-
Privilege Escalation: A user suddenly accessing resources they don't
normally have permissions for.
III. Integrating Threat Intelligence: Adding Context to the Clues
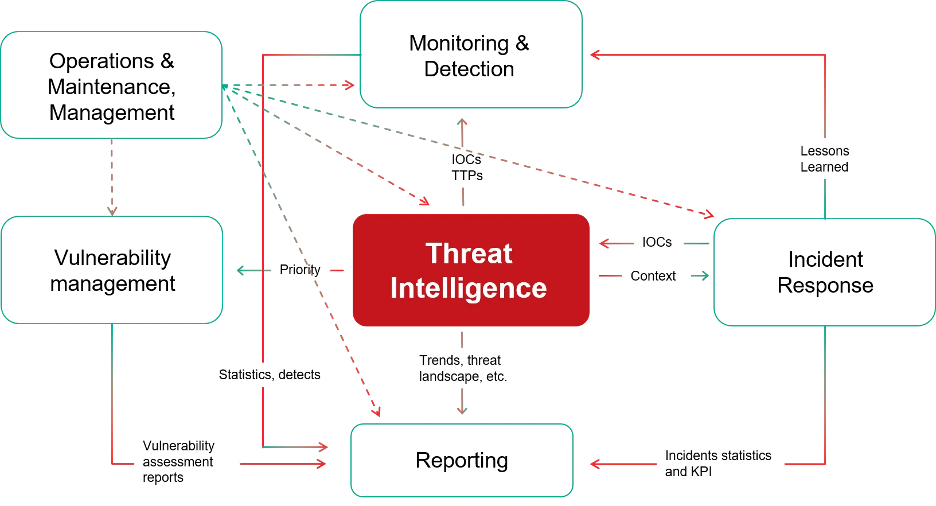
Threat intelligence provides crucial context to log data, helping to identify
known malicious actors and indicators of compromise (IOCs).
Enriching Logs:
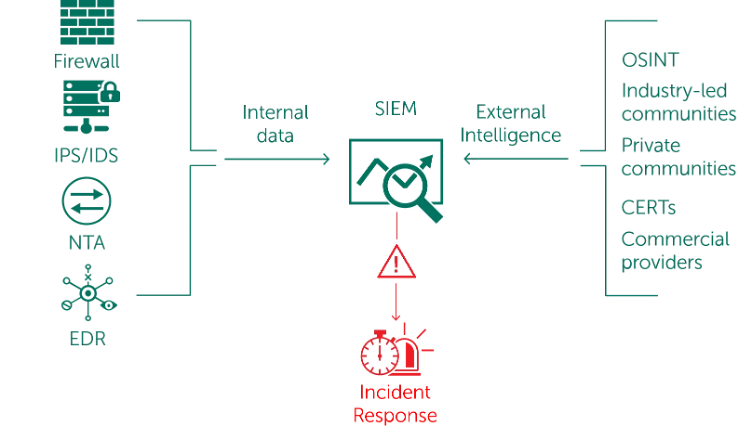
-
Threat Intelligence Feeds: Use feeds like AlienVault OTX,
MISP, or commercial providers.
-
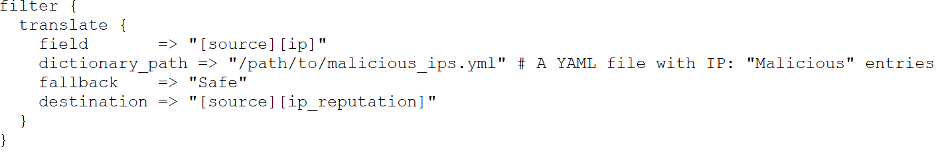
Example (IP Reputation Check): Use Logstash's
translate filter or a similar mechanism in your log management
solution to check each source IP address against a list of known malicious
IPs (downloaded regularly from a threat intel feed).
IOC Hunting:
-
Example (Searching for a Known Malicious Hash in File Access Logs):
event.action: "file_access" AND file.hash.sha256:
"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"
Automating Threat Intelligence-Driven Analysis:
-
Threat Intelligence Platforms (TIPs): Platforms like
ThreatConnect or Anomali can help manage and operationalize
threat intelligence.
-
SOAR Integration: Integrate your log analysis platform with a SOAR
solution (e.g., Demisto, Phantom) to automate responses to
threats identified through log analysis enriched with threat intel.
IV. Case Study: Deconstructing a Real-World Attack (Inspired by the
SolarWinds Breach)
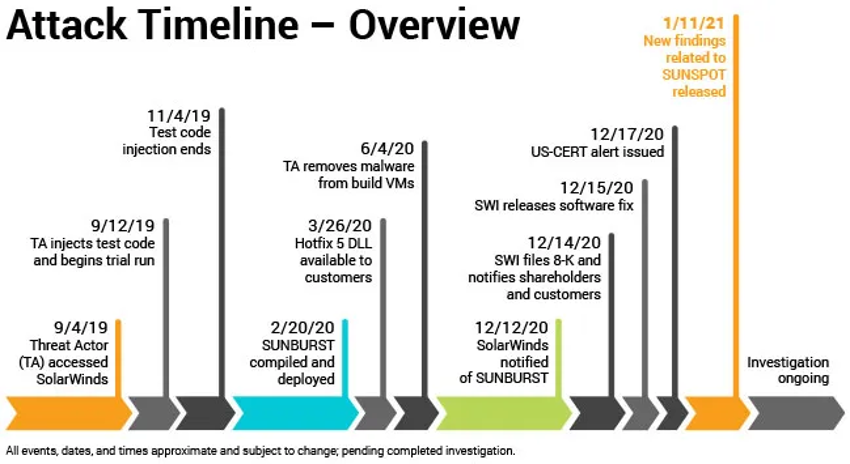
Let's analyze a hypothetical attack scenario inspired by the SolarWinds supply
chain compromise, focusing on how advanced log analysis could have helped
uncover the intrusion.
-
Attack Overview: Attackers compromised the build system of a widely
used IT management software (similar to SolarWinds Orion). They injected
malicious code into a software update, which was then distributed to
thousands of customers. The malicious code created a backdoor, allowing
attackers to gain remote access to customer networks. The attackers moved
laterally, escalating privileges and stealing sensitive data.
-
Initial Detection: In this scenario, let's assume the initial
detection came from an anomaly detected in the network traffic monitoring
system—an unusual spike in outbound traffic to an unfamiliar domain.
-
Crucial Log Data:
-
Build Server Logs: Logs from the compromised build server would
(ideally) have shown unusual code modifications, access by unauthorized
users, or connections to suspicious external systems.
-
DNS Logs: Would have revealed queries to the attacker's
command-and-control (C2) server.
-
Authentication Logs: Showed successful logins from unusual
locations or using compromised accounts.
-
Process Execution Logs: On compromised systems, these logs might
have captured the execution of the malicious code.
-
Network Traffic Logs: Indicated data exfiltration to the
attacker's infrastructure.
-
Correlation and Sequencing: Suspicious build event → software update
distribution → DNS queries to C2 server → successful logins from unusual
locations → data exfiltration.
-
Anomaly Detection: Deviations in build processes, unusual network
traffic patterns, anomalous user behavior.
-
Threat Intelligence Role: If the attacker's C2 domain or the hash of
the malicious code were known and available in threat intelligence feeds,
the analysis would have been significantly accelerated.
-
Lessons Learned: The importance of comprehensive logging, the power
of correlation, the value of anomaly detection, and the need for threat
intelligence.
V. Future Trends in Log Analysis

-
AI and Machine Learning Evolution: Expect more sophisticated AI/ML
algorithms for anomaly detection, automated threat hunting, and predictive
analysis.
-
Cloud-Native Log Analysis: Solutions tailored for cloud-native
environments (serverless, containers) will become increasingly important.
-
Privacy and Compliance Considerations: Regulations like GDPR will
continue to shape how logs are collected, stored, and analyzed.
-
Extended Detection and Response (XDR): Log analysis will be a crucial
component of XDR platforms, which integrate data from multiple security
controls for a holistic view of the threat landscape.
VI. Conclusion: Mastering the Art

Log analysis is a critical skill for cybersecurity professionals in today's
threat landscape. It's not just about sifting through data; it's about
understanding the story that the data tells. By mastering advanced techniques
like log aggregation, data reduction, correlation, anomaly detection, and
threat intelligence integration, we can transform log data from a silent
witness into a powerful weapon against cyber threats.
The journey to becoming a log analysis expert is ongoing. Invest in developing
your skills, explore new tools and techniques, and stay updated on the latest
trends. Let's continue to refine the art of log analysis and strengthen our
defenses against the ever-evolving threats in the digital world.
VII. Call to Action
Looking ahead, how do you see AI and machine learning further transforming the
field of log analysis? What are your predictions for the next big advancements
in this area? I encourage you to share your thoughts, experiences, and
questions in the comments below. Let's build a community of log analysis
experts!
VIII. Resources








 This Splunk query searches for failed login attempts followed by a
successful login from the same IP address within a defined time window,
which could indicate a brute-force attack.
This Splunk query searches for failed login attempts followed by a
successful login from the same IP address within a defined time window,
which could indicate a brute-force attack.










