
In the ever-evolving landscape of cyber threats, Security Operations Centers (SOCs) stand as the frontline defenders, tirelessly safeguarding digital assets against a relentless barrage of sophisticated attacks. These dedicated teams of cyber professionals are the unseen guardians, working around the clock to detect, analyze, and respond to security incidents. But what empowers these guardians to effectively combat the myriad of threats lurking in the digital shadows? The answer lies in their arsenal – a comprehensive suite of cutting-edge tools that transform raw data into actionable intelligence, enabling them to uncover hidden threats and fortify defenses.
This guide is meticulously crafted for aspiring and seasoned SOC analysts, cybersecurity enthusiasts, and organizations seeking to understand the essential tools that form the backbone of a robust security posture. Inspired by real-world challenges and the dynamic nature of cyber warfare, we will delve deep into the functionalities, benefits, and strategic importance of the best SOC analyst tools available today. From the foundational pillars of Security Information and Event Management (SIEM) to the advanced capabilities of Extended Detection and Response (XDR) and the transformative power of Artificial Intelligence, prepare to embark on a journey that unveils the critical instruments shaping the future of cybersecurity.
Join us as we explore how these tools empower SOC analysts to navigate the complexities of modern cyber threats, turning the tide against adversaries and ensuring the resilience of our digital world. Whether you're looking to enhance your skills, optimize your SOC operations, or simply gain a deeper understanding of the technologies that protect us, this guide will serve as your definitive resource.
At the heart of every effective Security Operations Center lies a set of foundational tools that serve as the bedrock for threat detection, analysis, and response. These core instruments are indispensable for any SOC analyst aiming to maintain a vigilant watch over an organization's digital assets. Let's explore these essential categories and the prominent tools within them.
In the collaborative spirit of cybersecurity, the community has developed and maintains numerous open-source and free tools that provide invaluable capabilities for SOC analysts. These platforms democratize access to advanced malware analysis, threat intelligence, and forensic capabilities, enabling organizations of all sizes to enhance their security posture without significant financial investment.
Why Open Source and Community Tools are Crucial:
Leading Open Source/Community Malware Analysis Platforms:
| Feature/Tool | VirusTotal | Hybrid Analysis | Triage (Hatching) | Any.run |
|---|---|---|---|---|
| Deployment | Cloud-based (Free tier available) | Cloud-based (Free tier available) | Cloud-based (Free tier available) | Cloud-based (interactive, free tier available) |
| Cost | Free (with premium options) | Free (with premium options) | Free (with premium options) | Free (with premium options) |
| Analysis Types | Static + Dynamic analysis | Dynamic analysis, behavioral analysis | Dynamic analysis, configuration extraction | Interactive dynamic analysis (manual/auto) |
| File Size Limits | 650MB (free), larger with premium | 100MB (free), larger with premium | 100MB (free), larger with premium | 16MB (free), larger with premium |
| Supported Formats | Executables, documents, archives, URLs | Executables, documents, scripts | Executables, documents, scripts, URLs | Executables, documents, scripts, URLs |
| Key Strengths | AV engine coverage (70+), historical data, community comments | Detailed behavioral analysis, network traffic, screenshots | Advanced configuration extraction, family detection, YARA | Real-time analysis, user interaction, behavior mapping |
| Community Features | Comments, voting, hunting rules | Public/private analysis, sharing | Public submissions, IOC extraction | Public submissions, task sharing, replay |
| API Access | Yes (rate-limited for free users) | Yes (rate-limited for free users) | Yes (rate-limited for free users) | Yes (limited access for free users) |
| Ideal For | Quick malware verification, IOC enrichment | Behavioral analysis, capability mapping | Threat research, config extraction | Hands-on dynamic analysis, training, education |
Why These Tools are Popular:

VirusTotal stands as the most widely recognized malware analysis platform globally, processing over 2 million files daily. Its popularity stems from its comprehensive coverage of antivirus engines (70+), making it the go-to tool for quick malware verification. The platform's strength lies in its vast database of historical analysis data and its integration capabilities with other security tools through APIs.
Hybrid Analysis (powered by Falcon Sandbox) has gained significant traction for its detailed behavioral analysis capabilities. It provides comprehensive reports showing exactly what malware does when executed, including file system changes, network communications, and process behavior. This granular visibility makes it invaluable for understanding attack techniques and developing countermeasures.
Triage by Hatching has emerged as a powerful platform for advanced malware analysis, particularly praised for its configuration extraction capabilities and family detection. It excels at identifying malware families and extracting C2 infrastructure information, making it a favorite among threat researchers and incident response teams.
ANY.RUN offers a uniquely interactive malware sandbox, allowing users to actively engage with live malware during runtime — click buttons, open windows, or trigger payloads as needed. This real-time interactivity, combined with its visual timeline and detailed process/network tracking, makes it highly valuable for training, reverse engineering, and hands-on analysis. Its ease of use and visual insight also appeal to beginners in malware analysis.
Leading Community Threat Intelligence Platforms:
| Feature/Tool | AlienVault OTX | URLVoid | Shodan |
|---|---|---|---|
| Primary Focus | Threat intelligence sharing | URL/Domain reputation | Internet-connected device discovery |
| Deployment | Cloud-based | Cloud-based | Cloud-based |
| Cost | Free | Free | Free tier with premium options |
| Data Sources | Community-contributed IOCs | Multiple URL scanners | Global internet scanning |
| Key Strengths | Collaborative intelligence sharing, pulse feeds, IOC correlation | Multi-engine URL analysis, reputation scoring | Device fingerprinting, vulnerability discovery, infrastructure analysis |
| API Access | Yes (free with registration) | Limited | Yes (free tier available) |
| Community Features | Pulse creation, following researchers, collaborative analysis | User submissions, reputation voting | Public queries, data sharing |
| Ideal For | Threat hunting, IOC enrichment, staying updated on threats | URL/domain verification, phishing detection | Infrastructure reconnaissance, attack surface discovery |
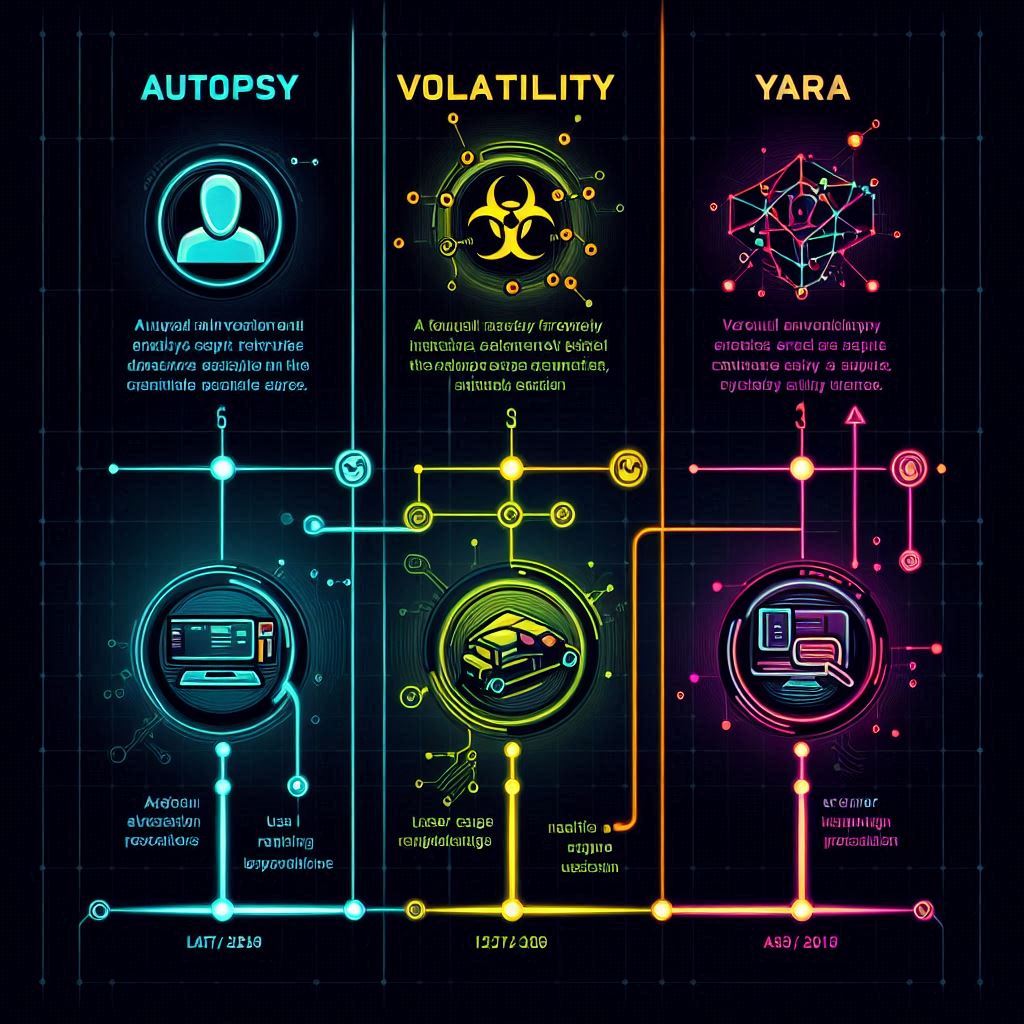
Essential Open Source Forensic Tools:
| Feature/Tool | Autopsy | Volatility | YARA |
|---|---|---|---|
| Primary Focus | Digital forensics platform | Memory analysis | Malware identification and classification |
| Deployment | Desktop application | Command-line tool | Command-line tool with GUI options |
| Cost | Free (Open source) | Free (Open source) | Free (Open source) |
| Key Strengths | Timeline analysis, keyword searching, file recovery | Memory dump analysis, process investigation | Pattern matching, rule-based detection |
| Learning Curve | Moderate | Steep | Moderate |
| Community Support | Strong | Very strong | Very strong |
| Ideal For | Incident response, digital forensics | Memory forensics, malware analysis | Malware detection, threat hunting |
Open Source Network Analysis Tools:
| Feature/Tool | Security Onion | Suricata | Zeek (Bro) |
|---|---|---|---|
| Primary Focus | Network security monitoring platform | Network IDS/IPS | Network traffic analysis |
| Deployment | Linux distribution | Network appliance/software | Network sensor |
| Cost | Free (Open source) | Free (Open source) | Free (Open source) |
| Key Strengths | Integrated NSM tools, easy deployment | High-performance threat detection | Rich metadata generation |
| Scalability | High | High | High |
| Community Support | Strong | Very strong | Very strong |
| Ideal For | Complete NSM solution | Network threat detection | Network behavior analysis |

Open Source Intelligence (OSINT) tools are critical for cybersecurity analysts to investigate, enrich, and validate indicators of compromise (IOCs). These tools provide access to vast amounts of publicly available data — including file hashes, IP reputation, domain registration, malware behavior, and leaked credentials — helping analysts respond to threats with speed and accuracy.
Using OSINT, analysts can:
These tools enhance situational awareness during threat investigations, making them an essential part of any security team's toolkit — from SOCs and threat hunters to red teamers and incident responders.
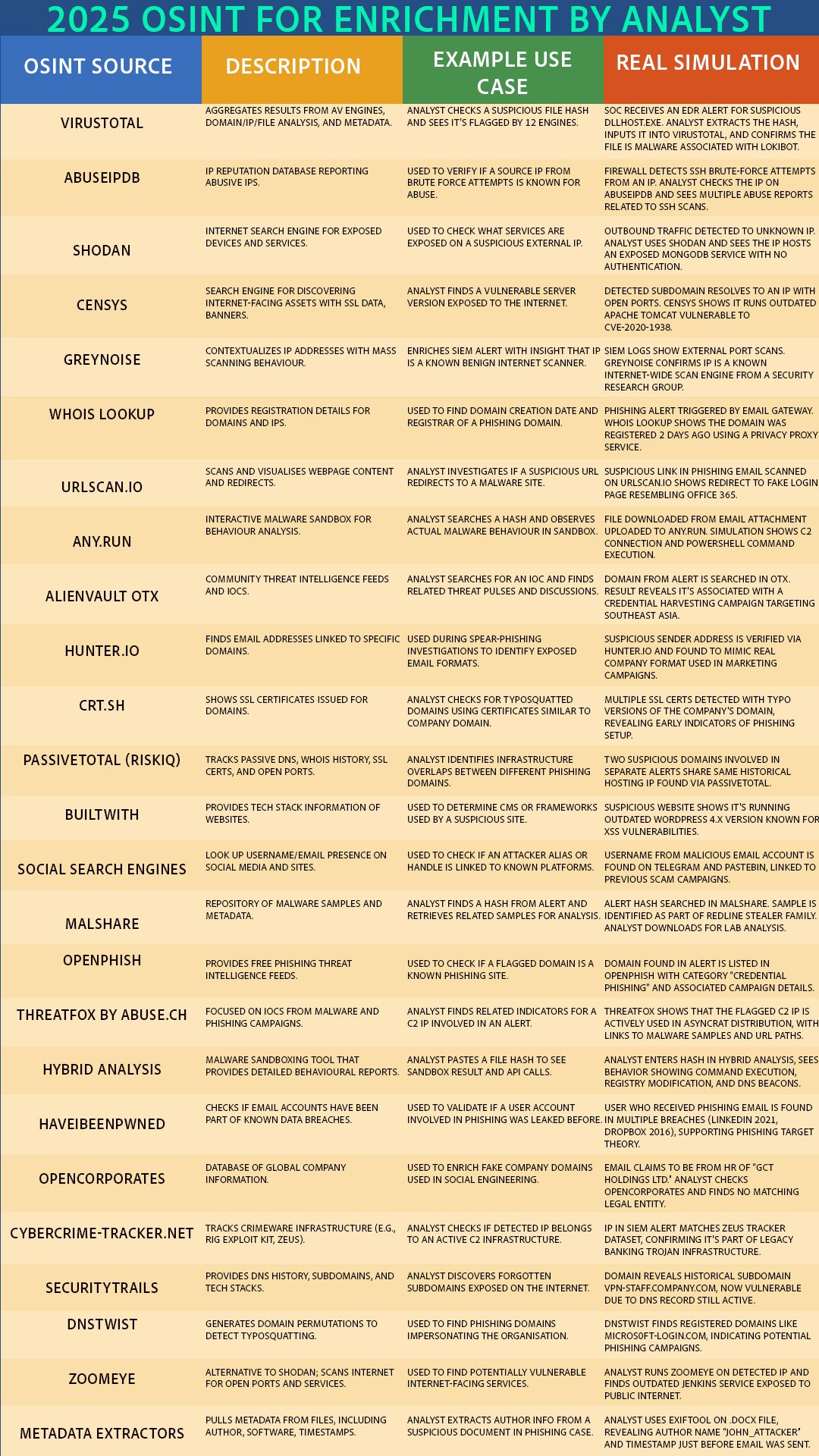
Workflow Integration Examples:
Operational Considerations:
Why These Tools Are Essential:
These open-source and community-driven tools represent the democratization of advanced cybersecurity capabilities. They enable SOC analysts to perform sophisticated analysis without significant budget constraints, while benefiting from the collective intelligence of the global security community. The collaborative nature of these platforms means that threats identified by one analyst can quickly benefit defenders worldwide, creating a powerful network effect in cyber defense.
The integration of these tools into SOC operations creates a more comprehensive and cost-effective security posture, while also providing valuable learning opportunities for analysts to develop advanced skills in malware analysis, threat hunting, and digital forensics.
While technology forms the backbone of modern SOC operations, the human element remains the most critical component. Highly skilled and continuously evolving SOC analysts are indispensable, bringing expertise, intuition, and critical thinking that no automated system can fully replicate. The effectiveness of even the most advanced tools hinges on the proficiency of the analysts wielding them [12].
SOC analysts are not merely operators of security tools; they are detectives, problem-solvers, and strategic thinkers. Their responsibilities extend beyond monitoring alerts to include:
The cybersecurity landscape is in a constant state of flux, with new threats and technologies emerging regularly. For SOC analysts, continuous learning is not just an advantage but a necessity. Organizations must invest in ongoing training and development programs to ensure their teams are equipped with the latest knowledge and skills.
Key Areas for Development:
Effective communication and collaboration within the SOC team, and with other departments, are crucial for successful threat management. A collaborative environment where analysts can share insights, knowledge, and experiences leads to faster incident resolution and a stronger collective defense.

In the dynamic and often perilous world of cybersecurity, the Security Operations Center stands as a critical bastion against an ever-growing tide of threats. The effectiveness of a SOC, however, is not solely determined by the sophistication of its technology, but by the strategic integration of the right tools, the adoption of forward-thinking methodologies, and, most importantly, the expertise and dedication of its human analysts.
This guide has traversed the landscape of essential SOC analyst tools, from the foundational SIEM and EDR systems that provide real-time visibility and endpoint protection, to the advanced capabilities of SOAR and XDR that promise automation and a unified threat view. We’ve also explored the transformative power of AI/ML in threat detection, the necessity of cloud-native security, and the paradigm shift brought about by Zero Trust Architecture. Underlying all these technological advancements is the undeniable truth: the human element remains paramount. The SOC analyst, with their critical thinking, investigative prowess, and commitment to continuous learning, is the ultimate force multiplier in the fight against cybercrime.
Mastering this diverse arsenal of tools and understanding the evolving trends is not merely about technical proficiency; it’s about cultivating a mindset of proactive defense, adaptability, and relentless vigilance. As the digital realm continues to expand and threats become more elusive, the role of the SOC analyst will only grow in importance. By embracing these tools and fostering a culture of continuous improvement, we can collectively strengthen our digital defenses and secure a more resilient future.
Are you ready to elevate your cybersecurity career and become a pivotal part of the digital defense frontline? The demand for skilled SOC analysts is soaring, and with the right knowledge and tools, you can make a significant impact. Explore our platform to discover training programs, certifications, and resources designed to equip you with the expertise needed to master these essential SOC analyst tools and navigate the complexities of modern cyber threats. Join a community of passionate cyber defenders and contribute to building a safer digital world.
What are your thoughts on the evolving landscape of SOC tools? Which tools do you find most impactful in your daily operations, and what emerging trends do you believe will redefine the future of cybersecurity? Share your insights and experiences in the comments below – let’s foster a vibrant discussion and collectively advance the art of cyber defense!